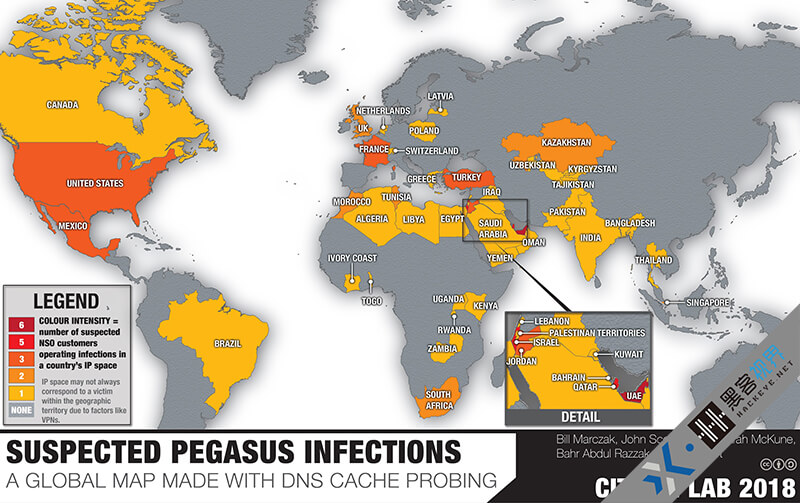
Spyware in News
Mobile phone users worldwide encounter over 9.5 Million spyware attacks.
Over 45 countries are infected by mobile spywares
Source : blog.360totalsecurity.com
Pegasus Spyware: A Global Threat to Privacy and Civil Liberties
In the digital age, surveillance technologies have evolved rapidly, with Pegasus spyware emerging as one of the most sophisticated tools. Developed by the Israeli cyber-intelligence firm NSO Group, Pegasus has been marketed as a means to combat terrorism and serious crimes. However, investigations have revealed its misuse by various governments to target journalists, activists, and political opponents, raising significant concerns about privacy and human rights.
Understanding Pegasus Spyware
Pegasus is designed to infiltrate smartphones running iOS and Android operating systems. It can be installed covertly, often without any action from the target — a method known as a “zero-click” exploit. Once installed, it grants the attacker access to a wide range of data, including text messages, emails, contacts, photos, and can activate the device’s microphone and camera for real-time surveillance. The spyware is modular, allowing operators to customize its functionalities based on specific surveillance needs.
NSO Group claims that Pegasus is sold exclusively to vetted government agencies for legitimate security purposes. However, reports have documented its use in various controversial contexts, highlighting the potential for Pegasus to be used as a tool for political repression rather than legitimate law enforcement.
Global Deployment and Misuse
Mexico
In Mexico, Pegasus spyware has been used to monitor journalists and human rights activists. Despite the government’s assurances to cease its use, investigations revealed that the Mexican Armed Forces continued to deploy Pegasus to spy on communications between journalists at the newspaper El Universal and human rights defender Raymundo Ramos. These actions have raised serious concerns about the violation of privacy and the suppression of free speech in the country.
Saudi Arabia
Saudi Arabia has been implicated in the use of Pegasus spyware to surveil associates of journalist Jamal Khashoggi prior to his assassination. Forensic analyses indicated that the phones of those close to Khashoggi were targeted before and after his murder, suggesting a coordinated effort to monitor and suppress dissenting voices.
Hungary
In Hungary, the government acknowledged purchasing Pegasus spyware, which was allegedly used to target journalists, businesspeople, and opposition politicians. This revelation has led to legal actions against the Hungarian state and NSO Group, highlighting concerns about the misuse of surveillance tools to stifle political opposition and press freedom.
Jordan
In Jordan, Pegasus spyware was used to hack the cellphones of at least 30 individuals, including journalists, lawyers, human rights, and political activists. The digital rights group Access Now reported that the hacking occurred from early 2020 until November 2023, raising alarms about the infringement of civil liberties and the targeting of civil society members in the country.
Indonesia
Investigations by Amnesty International and media partners have uncovered evidence that Indonesian state agencies, including the national police and intelligence bodies, have acquired and utilized Pegasus spyware. Between 2017 and 2023, these tools were reportedly used to monitor politicians, activists, journalists, and civil society members. The procurement often involved complex networks of suppliers and intermediaries, sometimes circumventing direct dealings with Israeli firms due to the absence of formal diplomatic relations.
Legal and Ethical Implications
The misuse of Pegasus has led to significant legal challenges for NSO Group. In December 2024, a U.S. federal judge ruled that NSO violated U.S. hacking laws and WhatsApp’s terms of service by using Pegasus to surveil over 1,400 individuals. This ruling marked a pivotal moment in holding spyware manufacturers accountable for their tools’ misuse.
The deployment of Pegasus spyware underscores the urgent need for robust oversight and regulation of surveillance technologies. As the line between national security and individual privacy blurs, it’s imperative for democratic societies to ensure that tools designed to protect do not become instruments of oppression.

Alert! Don’t fall for these 4 online shopping scams that could ruin your festive season
Fake shopping websites
As I mentioned previously, the festive season calls for a lot of shopping. Scammers have created many fake shopping websites that pretty much look like the real ones. The fake links are shared along with festive wishes on WhatsApp, mail, or SMS. Once the users go to these websites, they often end up getting scammed, the product never gets delivered, and often their personal data is misused too.IRCTC application scam
People travel a lot during the festive season and now a fake IRCTC website has been identified that steals users’ data when comes to booking their tickets. The fake website is lined with spyware that steals credentials from Facebook and Google, extracts codes from Google Authenticator, tracks GPS locations, and can even use the device’s camera to capture videos.Gift card scam
Scammers also send fake messages stating that a user has won a certain prize or gift card. Such messages often read, “Dear customer, congratulations! You have won….” They ask users to claim this by clicking on a link. The link directs them to malicious websites where users’ personal data is compromised.Banking reward scams
Under this scam, fraudsters will lure you into downloading harmful APK files. Urgency messages such as “available only today” or “last day to avail” will be added to create a sense of urgency. With these links, they will promise some exciting prices or will say that your account has been blocked due to a KYC error or something and hence you should do the required work urgently. And once you click on these links you might lose out on your money, your personal data can be misused, etc. Read More: https://www.digit.in/news/general/alert-dont-fall-for-these-4-online-shopping-scams-that-could-ruin-your-festive-season.html Source Credit: https://www.digit.in/
Email scam in Indiana relies on ‘Pegasus spyware’
Network Indiana
STATEWIDE — Indiana State Police are warning the public to be aware of an email extortion scam that’s surfaced in Indiana. Cybercrime detectives say this one has been happening repetitively for the last couple of months. “It shows up as an email. The scammer has done homework on the target. They have a lot of personal information that they will use to confirm what that person knows is real,” said Indiana State Police Sergeant John Perrine in Indianapolis. The scammer will tell the person that they have installed Pegasus spyware on the target’s phone and then attempt to extort money from them. “Pegasus spyware is a very specific software that has not been found to be used in the private market yet. So if anyone says they have this on a private citizen, then that’s just a red flag that’s simply not true,” said Perrine. On a bigger level, Perrine says you need to be mindful that scammers are becoming more sophisticated in their nefarious ways. “They prey on information that people are sensitive about and then they use that information to prey on them. So if something doesn’t seem right to you, it probably isn’t right,” said Perrine. Read More: https://www.newsnowwarsaw.com/email-scam-in-indiana-relies-on-pegasus-spyware/ Source Credit: www.newsnowwarsaw.com
Millions of Android users placed on red alert and told to follow 3 critical rules
It appears that a few apps on Google's Play Store have also been infected with Necro making this ab even more worrying threat.
According to Kaspersky, one application called Wuta Camera was downloaded over 10 million times from Google Play before Necro was discovered and removed from the photo editing service. Now, in a bid to stop more users from becoming a victim of Necro, Kaspersky has issued some vital advice which you are wise not to ignore. • Kaspersky strongly advises against downloading apps from unofficial sources because the risk of device infection is extremely high. Secondly, apps on Google Play and other official platforms should also be treated with a healthy dose of skepticism. Even a popular app like Wuta Camera, with 10 million downloads, proved powerless in the face of Necro. Make sure to protect your devices so as not to be caught off guard by a Trojan. • Check the app page in the store before downloading. Kaspersky says it recommends looking at reviews with low ratings, as these generally give heads-up about potential pitfalls. Rave reviews could be fake, while a high overall score is easy to inflate. • Don’t look for mods or hacked versions. Such apps are almost always stuffed with all kinds of Trojans: from the most harmless to mobile spyware like CanesSpy. Read More: https://www.mirror.co.uk/tech/android-warning-necro-attack-app-33755973 Source Credit: https://www.mirror.co.uk/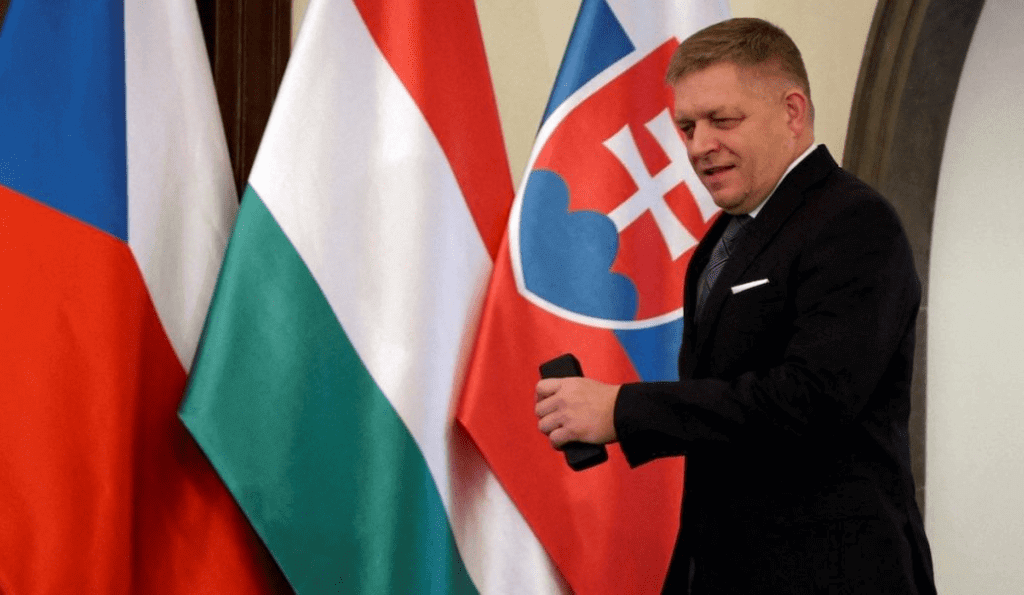
Big Brother in Bratislava: Does Robert Fico have Pegasus?

New Octo Android malware version impersonates NordVPN, Google Chrome
ThreatFabric also notes that Octo2 now receives a list of apps to intercept and block push notifications from, allowing the operators to refine their targeting scope.
Octo2 has not been spotted on Google Play, so its distribution is currently believed to be limited to third-party app stores, which Android users should avoid. Read More: https://www.bleepingcomputer.com/news/security/new-octo-android-malware-version-impersonates-nordvpn-google-chrome/ Source Credit: https://www.bleepingcomputer.com/
Pegasus: UK-based spyware victims ask police to investigate hacking

Pegasus Spyware Victims Ask U.K. Police to Charge Shadowy NSO Group
Hacked on British Soil
Alongside Altikriti, the hacking victims include include Azzam Tamimi, a Palestinian-born British journalist and academic, a prominent critic of the Saudi regime; Mohammed Kozbar, a Lebanese-born British citizen and the leader of the Finsbury Park mosque; and Yusuf Al Jamri, a Bahraini human rights activist who was granted asylum in the U.K. All were hacked between 2018 and 2021 on British soil. Their complaint to the police is being made against NSO Group and its board members; the firm’s parent company Luxembourg-based Q Cyber Technologies; London-based private equity firm Novalpina, which bought NSO in 2019. The human rights activists are alleging the people involved with NSO breached the U.K.’s Computer Misuse Act by enabling state actors to hack their phones using Pegasus. (Novalpina did not respond to a request for comment.) The hackers in question are believed to be the Kingdom of Saudi Arabia, the UAE, and the Kingdom of Bahrain. The U.K. recently became more significant to NSO’s operations. In 2023, the management of five NSO-linked companies was moved to London and two U.K.-based officers were appointed. Meanwhile, NSO continues to face a slew of civil cases in the U.S., with the company moving for dismissal in lawsuits by hacked Salvadoran journalists and Hanan Elatr Khashoggi, the widow of murdered journalist Jamal Khashoggi. Last week, Apple asked a court in San Francisco to dismiss its three-year hacking suit against NSO, after Israeli officials took files from NSO’s headquarters — an apparent attempt to frustrate lawsuits in the U.S. Apple argued it may now never be able to get the most critical files about Pegasus and that the revelation of its own defensive systems in court might aid other spyware companies. “NSO is very vigorously defending these lawsuits,” said Stephanie Krent, attorney at the Knight First Amendment Institute. “It is trying to draw litigation out and really avoid being held to account.”“Absolute Non-reaction”
In July 2021, Altikriti was notified by The Guardian as part of its Pegasus Project that his number was on a leaked list of those suspected to be hacked. According to The Guardian, Altikriti’s phone number was on a list of people of interest to the UAE given to NSO. Altikriti was concerned but not surprised. For many years, he had been vocally critical of the UAE, where he previously lived. The UAE designated his organization, the Cordoba Foundation — which works to promote dialogue and rapprochement between Islam and the West — as a terrorist group in 2014. In response, the organization issued a statement calling the country a “despotic regime seeking to silence any form of dissent.” He made similar declarations about the UAE over the following years. Around the time Altikriti was hacked in July 2020, he had been working on several hostage release deals, mainly in the Middle East. He alleges that phone hacking interfered with his communications related to one deal. After he was notified of the potential hack, Altikriti’s phone was tested by Amnesty International and Citizen Lab at the University of Toronto, which studies cyber issues affecting human rights. The hack was confirmed. Altikriti quickly went public about the cyberattack, posting a statement calling on the U.K. government to stand against the use of such spyware. Altikriti has since become increasingly frustrated by the lack of action. “You think that the U.K. Government, having seen a number of its own citizens and those on its lands being violated in the way that we have evidence now, would do something,” Altrikiti told The Intercept. “But so far we have seen an absolute non-reaction.” In 2022, Altikriti and Kozbar, one of the other human rights activists behind the complaint to police, sent a pre-claim notice to NSO, the UAE, and Saudi Arabia, of their intention to file a civil suit over the alleged Pegasus phone hacking. In formal response letter obtained by The Intercept, NSO said there was “no basis for the claims.” The company said that since Q Cyber Technologies Ltd and NSO Group Technologies Ltd are each lsraeli companies and neither was present in England and Wales, English courts had no jurisdiction over them. They also argued that the claims were barred by state immunity because, if the alleged attacks happened, they were conducted on behalf of foreign governments who are immune from prosecution. In Wednesday’s complaint to police, other claimants have stories similar to Altikriti. Al Jamri was active on social media promoting awareness of human rights abuses and political issues in Bahrain. In 2011, he was politically active during the Arab Spring. In its wake, he was regularly subjected to interrogation and harassment by authorities. He was detained for the third time in August 2017 and subjected to torture. Upon his release, he sought asylum in the U.K. Two years later, Al Jamri was targeted with Pegasus by servers traced to Bahrain, according to Citizen Lab. This happened around the same time he was posting about an incident at the British Embassy of Bahrain, when a dissident was allegedly assaulted by staff. In August 2019, like Altikriti, Al Jamri was notified by The Guardian, and his phone was subsequently tested and confirmed to have infections. He also went public about the hack.U.S. Lawsuits
Despite Apple’s attempt to withdraw its case, NSO still faces a slew of lawsuits in the U.S. In October 2019, WhatsApp filed a lawsuit against the Israeli company for using its platform to hack the phones of 1,400 of the chat app’s users. NSO has repeatedly tried to get the case thrown out, including by claiming sovereign immunity — that it acted as an agent of foreign governments — though that effort was rejected in January. In November 2021, the same month NSO was blacklisted by the U.S. government for its role enabling human rights abuses, Apple also filed its case against NSO to hold it accountable for the surveillance and targeting of its users. On September 13, the company moved to dismiss its case, saying that Israeli officials’ seizure of NSO documents “were part of an unusual legal maneuver created by Israel to block the disclosure of information about Pegasus.” NSO is known to have a close relationship with the Israeli government, which it claims to have been working with during Israel’s war on Gaza. In November, in an attempt to rehabilitate its image, NSO sent an urgent letter to request a meeting with Secretary of State Antony Blinken and officials at the U.S. State Department, citing the threat of Hamas. In 2022, the Knight Institute filed its lawsuit on behalf of current and former journalists of El Faro, one of Central America’s leading independent news organizations, based in El Salvador. It was the first case filed by journalists against NSO in U.S. court. A judge dismissed the case in March, but it is currently on appeal. “We felt it was important that victims have access to courts in order to hold NSO Group to account,” said Krent, the Knight attorney. “At the end of the day, they are facing the most serious threats from the use of this spyware.” Read More: https://theintercept.com/2024/09/19/pegasus-spyware-nso-group-uk/ Source Credit: https://theintercept.com/
‘Predator’ Spyware’s Makers Draw More Sanctions From the US
The US has imposed new sanctions related to the Intellexa Consortium, a web of companies that makes “Predator” spyware products that Biden administration officials say have been used to target American officials and enable human rights abuses.

Apple dismisses lawsuit against surveillance firm NSO Group due to risk of threat intelligence exposure
Apple drops its lawsuit against commercial spyware vendor NSO Group, due to the risk of “threat intelligence” information exposure.
Apple is seeking to drop its lawsuit against Israeli spyware company NSO Group, citing the risk of “threat intelligence” information exposure. Apple wants to dismiss its lawsuit against NSO Group due to three key developments. First, continuing the lawsuit could compromise advanced threat intelligence gathered by Apple by exposing sensitive information to third parties. Second, the spyware industry has diversified, making a lawsuit against NSO less impactful, as other spyware companies continue their operations. Third, obstacles in obtaining critical information from NSO undermine the effectiveness of the legal action. Apple pointed out that it prefers to focus its efforts on developing technical measures to protect users from spyware like Pegasus. The IT giant fears that the disclosures of its threat intelligence related to commercial spyware operations could aid NSO and other surveillance firms. “Apple’s teams work tirelessly to protect the critical threat-intelligence information that Apple uses to protect its users worldwide. Because of these efforts, along with the efforts of others in the industry and national governments to combat the rise of commercial spyware, Defendants have been substantially weakened.” reads the court filing. “At the same time, unfortunately, other malicious actors have arisen in the commercial spyware industry. It is because of this combination of factors that Apple now seeks voluntary dismissal of this case.” reads The court filing referenced an article published by The Guardian article reporting that Israeli officials seized files from NSO Group’s headquarters. “The Israeli government took extraordinary measures to frustrate a high-stakes US lawsuit that threatened to reveal closely guarded secrets about one of the world’s most notorious hacking tools, leaked files suggest.” reads the article published by the Guardian mentioned in the court filing. “Israeli officials seized documents about Pegasus spyware from its manufacturer, NSO Group, in an effort to prevent the company from being able to comply with demands made by WhatsApp in a US court to hand over information about the invasive technology.” The officials requested an Israeli court to keep this action secret, even from parties involved in Meta’s ongoing WhatsApp hacking lawsuit against NSO. The hacked Israeli ministry of justice communications revealed concerns that sensitive information could be accessed by Americans. “while Apple takes no position on the truth or falsity of the Guardian Story described above, its existence presents cause for concern about the potential for Apple to obtain the discovery it needs.” continues the court filing. In November 2021, Apple sued NSO Group and its parent company Q Cyber Technologies in a U.S. federal court for illegally targeting its customers with the surveillance spyware Pegasus. According to the lawsuit, NSO Group is accountable for hacking into Apple’s iOS-based devices using zero-click exploits. The software developed by the surveillance firm was used to spy on activists, journalists, researchers, and government officials. Apple also announced it would support with a contribution of $10 million to the academic research in unmasking the illegal surveillance activities “Apple today filed a lawsuit against NSO Group and its parent company to hold it accountable for the surveillance and targeting of Apple users. The complaint provides new information on how NSO Group infected victims’ devices with its Pegasus spyware. To prevent further abuse and harm to its users, Apple is also seeking a permanent injunction to ban NSO Group from using any Apple software, services, or devices.” reads the announcement published by Apple. The legal action aims at permanently preventing the infamous company from breaking into any Apple software, services, or devices. The complaint included details about the NSO Group’s FORCEDENTRY exploit that was used to target multiple users and drop the latest version of NSO Group’s Pegasus. Threat actors leveraged two zero-click iMessage exploits to infect the iPhones with spyware, respectively known as 2020 KISMET exploit and FORCEDENTRY. The latter exploit was discovered by Citizen Lab researchers, it is able to bypass the “BlastDoor” sandbox introduced early this year in iOS to block iMessage zero-click exp Read More: https://securityaffairs.com/168450/laws-and-regulations/apple-drops-lawsuit-against-nso-group.html Source Credit: https://securityaffairs.com/
Indian Intelligence used Israeli spyware to snoop on WhatsApp users
Pegasus, the spyware, is classified as a weapon by the Israeli Government. The NSO Group which develops and sells the spyware maintains that it sells them only to Government agencies

Predator spyware updated with dangerous new features, also now harder to track
Infosec in brief After activating its chameleon field and going to ground following press attention earlier this year, the dangerous Predator commercial spyware kit is back – with upgrades.…
Insikt Group, the threat research arm of cyber security firm Recorded Future, reported last week that new Predator infrastructure has popped up in countries like the Democratic Republic of the Congo and Angola, suggesting US sanctions applied to Intellexa, the spyware firm behind Predator, did not completely succeed.
"After Intellexa … faced sanctions and exposure, a noticeable reduction in Predator activity was observed," Insikt Group wrote in its report on Predator. "However, according to [our] recent analysis, Predator is far from disappearing."
Predator, like Pegasus from the NSO group and other commercial spyware, allows government actors to infiltrate devices and spy on users. The product is known for its ability to track locations, access device cameras, record calls, read messages and do other privacy-invading things.
The latest updates, unfortunately, mean Predator will be a lot harder to track.
According to Insikt, the Predator update it has spotted further anonymizes customer operations and makes it harder to locate users.
"This change makes it more difficult for researchers and cybersecurity defenders to track the spread of Predator," the researchers noted.
"Defenders can mitigate risks by following cyber security best practices, including regular device updates, using lockdown mode, and deploying mobile device management systems," Insikt recommends. "Given Predator's renewed presence and the sophistication of its infrastructure, individuals and organizations must stay vigilant."
Act now, and you might even protect yourself against Russian cyber spies using similar tactics, too.
X accounts belonging to two of former US president Donald Trump's family members were hijacked last week to push links to a scam version of Trump's forthcoming decentralized finance venture, in a pair of now-deleted Xeets.
Republican National Committee co-chair Lara Trump, and Donald Trump's daughter Tiffany, both posted about the launch of Trump's World Liberty Financial – a crypto platform the ex-president and current Republican nominee announced in late August as "the DeFiant Ones," but apparently already renamed.
The platform hasn't launched yet, and the spoof links went to a mystery website promising to be the only official source on the project.
World Liberty Financial – promoted by Trump as a way for everyday Americans to avoid being "squeezed by big banks and financial elites" – has raised concerns. Seventy percent of the tokens being minted when World Liberty is launched are supposed to go to project insiders – an amount crypto publication Coindesk noted is "unusually high."
A relatively new and nasty ransomware variant known as "Lost in the Fog" that targeted education and recreation institutions appears to have started targeting financial institutions.
According to security operations-as-a-service firm Adlumin, it spotted someone using Fog last month trying to break into a "mid-sized financial business using compromised VPN credentials." That type of attack is standard operating procedure for Fog.
Once inside a network, Fog uses advanced techniques like pass-the-hash attacks to escalate privileges, cripple network security, steal data and encrypt it with a ransom note. Fog hasn't been attributed to any known threat actor yet, which Adlumin said suggests it may come from a new, but "highly skilled" threat actor that appears to be based in Russia.
Standard ransomware prevention techniques apply here, folks – just be advised if you're in the financial sector that there's a hot new variant out there gunning for your systems, especially weak VPNs.
Security researchers monitoring open source packages have spotted nasty folk waiting for a package to be deleted and re-creating the repository with a malicious version.
Dubbed "revival hijack" by researchers at JFrog, the tactic involves abusing the Python Package Index's (PyPI) package registration system.
"This attack technique involves hijacking PyPI software packages by manipulating the option to re-register them once they're removed from PyPI's index by the original owner," the JFroggers wrote.
The DevOps and security firm estimates there are around 22,000 packages in PyPI vulnerable to a revive hijack attack, and the researchers noted they've already spotted the technique being used in the wild to infect the pingdomv3 package.
The result of a successful revive hijack could be disastrous – especially because it can be used to trick systems into thinking the malicious package is simply an updated version of the old, now deleted, official one.
"On average, 309 [PyPI] packages are removed each month," JFrog noted.
So start checking the age of repositories and the name of the maintainer before updating those packages, folks
A trio of computer science students, and their lecturer, have been charged with unauthorized access to computer data after discovering and presenting evidence of a security flaw.
Michael Debono, Giorgio Grigolo and Luke Bjorn Scerri were reportedly arrested in 2022 and recently charged, along with their lecturer Mark Joseph Vella, for unauthorized access, preventing or obstructing the input of data without authorization and obstructing or preventing the use of a computer system for vulnerability testing in FreeHour, a scheduling app for students.
After reporting the vulnerability to FreeHour and requesting a bounty, the trio were reportedly arrested instead. They are scheduled to head to trial next year on the matter.
While the United States and many other countries have some form of concession in place to not prosecute good-faith security researchers, Malta appears to have no such law. ®
Read More: https://www.msn.com/en-us/news/technology/predator-spyware-updated-with-dangerous-new-features-also-now-harder-to-track/ar-AA1qdU7m
Source Credit: https://www.msn.com/en-us/news

New Lookout Threat Research Proves Mobile Security Should Be Central to Modern Data Protection Strategies
- A substantial uptick of 40.4% in mobile phishing attempts and malicious web attacks targeting enterprise organizations.
- More than 80,000 malicious apps were detected on enterprise mobile devices. Mobile app threats can vary widely, from invasive permissions and riskware that pose significant compliance risks to sophisticated spyware capable of tracking devices, stealing data, eavesdropping on conversations and accessing the user’s camera and microphone.
- In Q2, Lookout protected customers against 47 new mobile malware families, and customers were given enhanced protection against 101 known mobile malware families.
- Top device misconfigurations include out-of-date OS, out-of-date Android Security Patch Levels (ASPL), no device lock and non-app store signer.
- The most critical families of mobile malware continued to lean heavily towards Android surveillanceware.
- The top ten most common mobile app vulnerabilities encountered by Lookout users in Q2 2024 were in components of mobile browsers. Since all mobile devices have a browser, attackers target these vulnerabilities, in particular, hoping users haven't updated to patched versions.
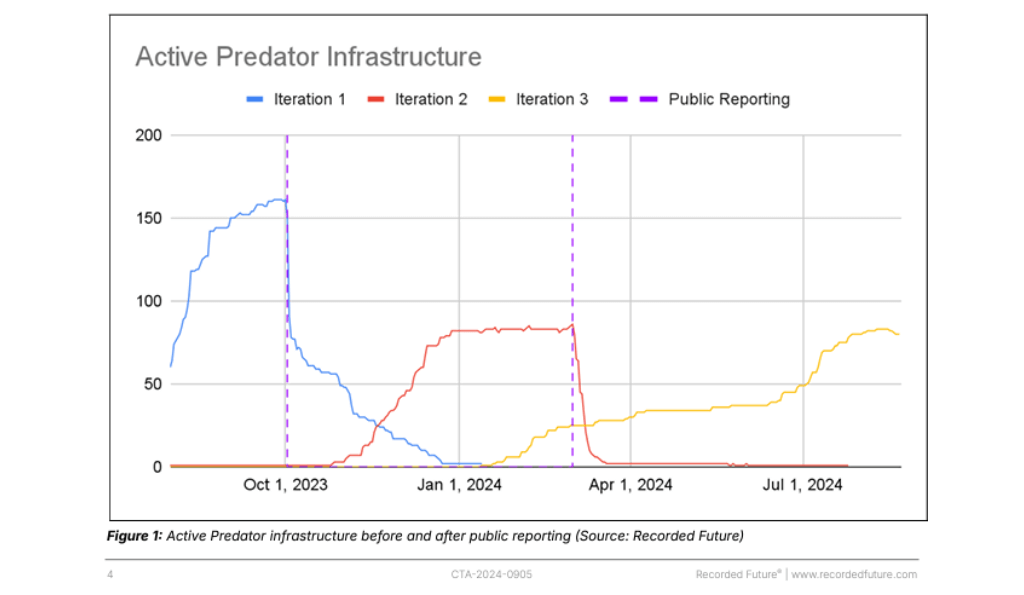
Predator spyware operation is back with a new infrastructure
Researchers warn of a fresh cluster of activity associated with the Predator spyware using a new infrastructure, following the U.S. sanctions against the Intellexa Consortium.
Recorded Future researchers warn that the Predator spyware has resurfaced with fresh infrastructure after a decline caused by US sanctions against Intellexa Consortium. In March 2024, the Department of the Treasury’s Office of Foreign Assets Control (OFAC) announced actions on two individuals and five entities associated with the Intellexa Consortium for their role in the development and distribution of the commercial Predator spyware used to target Americans. The surveillance software was also used to spy on U.S. government officials, journalists, and policy experts. The Department of the Treasury warns that the proliferation of commercial spyware poses growing risks to the United States. Surveillance software was misused by foreign actors in attacks aimed at dissidents and journalists around the world. The Intellexa Consortium was created in 2019, it has acted as a marketing umbrella for various offensive cyber companies that provide commercial spyware and surveillance tools designed for targeted and mass surveillance campaigns. The name “Predator” spyware was used to refer to a collection of surveillance tools that allows to compromise victims’ devices through zero-click attacks. Predator spyware is known for its extensive data-stealing and surveillance capabilities. In March 2023, the US Government issued an Executive Order on the prohibition on use by the United States Government of commercial spyware that poses risks to national security. In July 2023, the Commerce Department’s Bureau of Industry and Security (BIS) added surveillance technology vendors Intellexa and Cytrox to the Entity List for trafficking in cyber exploits used to gain access to information systems. Following the exposure of the Intellexa group’s operations and sanctions imposed by the US government experts reported a drop in the surveillance firm’s activity and its spyware Predator went out of the radar. Recorded Future now shows that the decline was likely associated with changes in TTPs adopted by the company in an attempt to evade detection. “This resurgence highlights Predator’s ongoing use by customers in countries such as the Democratic Republic of the Congo (DRC) and Angola.” reads the Recorded Future’s report. “While Predator continues to pose significant privacy and security risks, especially to high-profile individuals like politicians and executives, new infrastructure changes make tracking users more difficult. “ Predator spyware operators added several layers to enhance their infrastructure, anonymize operations and evade detection, making it harder to identify which countries are using the spyware. The researchers pointed out that despite these upgrades, the attack chain is unchanged, relying on both “one-click” and “zero-click” exploits as vectors, often exploiting browser vulnerabilities. While no fully remote zero-click attacks, like those seen with Pegasus, have been reported, Predator remains a significant threat, especially for targeting high-profile individuals. “One of the most concerning aspects of Predator’s return is its likely continued targeting of high-profile individuals. Politicians, executives, journalists, and activists are at the highest risk due to the intelligence value they hold for governments or other malicious actors. The costly licensing of Predator further suggests that operators reserve its use for strategic, high-value targets.” concludes the report. “This widespread use of mercenary spyware, particularly against political opposition, has sparked concern in regions like the European Union. Investigations in Greece and Poland have already revealed how spyware has been used against opposition figures and journalists, raising serious questions about the legality and ethics of such surveillance.” Recorded Future says. As the surveillance market grows, governments and cybersecurity professionals must stay proactive. In February, a report published by Google Threat Analysis Group (TAG), titled “Buying Spying, an in-depth report with our insights into Commercial Surveillance Vendors (CSVs)”, warned of the rise of commercial spyware vendors and the risks to free speech, the free press, and the open internet. The surveillance industry is experiencing exponential growth, fueled by the sustained demand from rogue governments, intelligence agencies, and malicious actors for sophisticated malware and surveillance tools. Read More: https://securityaffairs.com/168222/intelligence/predator-spyware-new-infrastructure.html Source Credit: https://securityaffairs.com/
Google releases new Pixel software update to remove security vulnerability
The potential security vulnerability had been found in all Pixel phones sold by Google across the world.
If you own a Google Pixel smartphone, don’t forget to update it with the latest version of the Android software to fix a major security loophole in the device.A few years ago, Google had reportedly installed a hidden app known as “Showcase.apk” on all Pixel handsets to enable in-store demos of the device at certain stores. Over time, the piece of software became inactive as it was no longer used.

Slovak spy agency has Pegasus spyware, opposition claims

Colombia to investigate police purchase of Pegasus spyware
Colombian President Gustavo Petro has ordered an investigation into the purchase of Pegasus spy software by the country's police force.
President Petro said the spyware was bought - in cash - from an Israeli surveillance firm during the government of his predecessor, Iván Duque.
He added that the software, which can be installed remotely on mobile phones to access people's microphones and cameras, may have been used to spy on political rivals, including himself.
The president's remarks were the first official confirmation that Colombia was among the countries which bought the phone malware.
Pegasus software infects iPhones and Android devices to enable operators to extract messages, photos and emails, record calls and secretly activate microphones and cameras.
Mr Petro revealed the news in a televised address to the nation, saying that he had learned of the purchase through a confidential document.
The president said that Colombia's police intelligence directorate (Dipol) had made two payments of $5.5m (£4.2m) each to Israeli surveillance firm NSO, which had developed the spyware.
NSO has said in the past that its software is intended for use against criminals and terrorists and is made available only to military, law enforcement and intelligence agencies from countries with good human rights records.
But Mr Petro queried how $11m in cash could have left the country without any trace of it being recorded in the published budget - and why.
"It is a laundering of assets made from our own state to disrupt the communications of whom?" he asked.
Pegasus spyware hit the headlines in 2021 when a list of 50,000 phone numbers of suspected victims of hacking was leaked to major media outlets.
Among those believed to have been targeted were activists, journalists and politicians from around the world.
President Petro urged the attorney-general's office to investigate the purchase and what police may have used the spyware for.
He also demanded that the head of Colombia's police force hand over all relevant documents related to Pegasus.
It is not the first time the Colombian security forces have been accused of illegally intercepting communication.
Wiretapping scandals have rocked the country repeatedly over the past two decades, leading to the closure of its intelligence agency, the Department of Administrative Services (DAS), in 2011.
Read More: https://www.bbc.com/news/articles/ckg5en18qvxo Source Credit: https://www.bbc.com
Mobile Spyware: A Potential Threat to Your Organization?
- Regular software updates: Keeping all mobile software up to date is crucial. Software updates are key since they typically include fixes for security flaws that spyware could potentially exploit.
- Cyber security training: It’s important to educate employees to identify threats such as suspicious applications and phishing emails. Awareness is a key defense mechanism in the fight against spyware.
- Robust security policies: Establishing and enforcing comprehensive security policies for mobile device usage can significantly reduce the risk of spyware infections. This includes regulating the installation of apps and the use of public Wi-Fi networks.
- Advanced security solutions: While the above best practices such as regular security updates, adequate training for employees, and clear security policies go a long way in improving security posture, it takes an advanced security solution to fully prevent and handle mobile spyware.

Android And iOS Users Attacked By Russian APT29 Hackers, Google Warns

Midnight Blizzard exploits iOS and Android via watering hole tactics
Powerful Spyware Exploits Enable a New String of ‘Watering Hole’ Attacks
Between November 2023 and July 2024, the attackers compromised Mongolian government websites and used the access to conduct “watering hole” attacks, in which anyone with a vulnerable device who loads a compromised website gets hacked. The attackers set up the malicious infrastructure to use exploits that “were identical or strikingly similar to exploits previously used by commercial surveillance vendors Intellexa and NSO Group,” Google’s TAG wrote on Thursday. The researchers say they “assess with moderate confidence” that the campaigns were carried out by APT29.
These spyware-esque hacking tools exploited vulnerabilities in Apple's iOS and Google's Android that had largely already been patched. Originally, they were deployed by the spyware vendors as unpatched, zero-day exploits, but in this iteration, the suspected Russian hackers were using them to target devices that hadn't been updated with these fixes.
“While we are uncertain how suspected APT29 actors acquired these exploits, our research underscores the extent to which exploits first developed by the commercial surveillance industry are proliferated to dangerous threat actors,” the TAG researchers wrote. “Moreover, watering hole attacks remain a threat where sophisticated exploits can be utilized to target those that visit sites regularly, including on mobile devices. Watering holes can still be an effective avenue for … mass targeting a population that might still run unpatched browsers.”
It is possible that the hackers purchased and adapted the spyware exploits or that they stole them or acquired them through a leak. It is also possible that the hackers were inspired by commercial exploits and reverse engineered them by examining infected victim devices.
Between November 2023 and February 2024, the hackers used an iOS and Safari exploit that was technically identical to an offering that Intellexa had first debuted a couple of months earlier as an unpatched zero-day in September 2023. In July 2024, the hackers also used a Chrome exploit adapted from an NSO Group tool that first appeared in May 2024. This latter hacking tool was used in combination with an exploit that had strong similarities to one Intellexa debuted back in September 2021.
When attackers exploit vulnerabilities that have already been patched, the activity is known as “n-day exploitation,” because the vulnerability still exists and can be abused in unpatched devices as time passes. The suspected Russian hackers incorporated the commercial spyware adjacent tools, but constructed their overall campaigns—including malware delivery and activity on compromised devices—differently than the typical commercial spyware customer would. This indicates a level of fluency and technical proficiency characteristic of an established and well-resourced state-backed hacking group.
“In each iteration of the watering hole campaigns, the attackers used exploits that were identical or strikingly similar to exploits from [commercial surveillance vendors], Intellexa and NSO Group,” TAG wrote. “We do not know how the attackers acquired these exploits. What is clear is that APT actors are using n-day exploits that were originally used as 0-days by CSVs.”
Read More: https://www.wired.com/story/russia-cozy-bear-watering-hole-attacks/ Source Credit: https://www.wired.com/
US announces new restrictions to curb global spyware industry
The US said it will impose global visa restrictions on individuals who have been involved in the misuse of commercial spyware, in a move that could affect major US allies including Israel, India, Jordan and Hungary.
The new policy, unveiled on Monday, underscores how the Biden administration continues to see the proliferation of weapons-grade commercial spyware – which has been used by governments around the world against hundreds of political dissidents, human rights advocates, journalists and lawyers – as a major threat to US national security and counterintelligence capabilities.
The move comes three years after the administration placed Israel’s NSO Group on a commerce department blacklist and issued an executive order prohibiting the US government’s own use of commercial spyware. Israeli companies lead the world in producing commercial spyware and the Biden administration’s tough stance on those companies has emerged as a diplomatic sore point between the two allies.
When it is successfully used against a target, spyware like NSO’s Pegasus can infiltrate any phone without a user knowing. Intelligence or other government agencies using a spyware like Pegasus can silently gain access to a mobile phone user’s photographs, phone conversations and texts, and messages shared via encrypted apps like WhatsApp and Signal. It can even be used as a remote listening device.
In a statement, Antony Blinken, the US secretary of state, said the misuse of commercial spyware has been linked to “arbitrary detentions, forced disappearances and extrajudicial killings in the most egregious of cases”.
It is not entirely clear what specific extrajudicial killing Blinken was referring to, but the Guardian and other media outlets have previously reported that close associates of the Saudi journalist Jamal Khashoggi had been targeted and hacked with Pegasus before his murder by Saudi agents inside the Saudi embassy in Istanbul in October 2018.
NSO has previously said its technology “was not associated in any way with the heinous murder of Jamal Khashoggi”.
For the US government, the proliferation of spyware – even when it is used by close allies – has for years been seen as a threat to security, especially against US government employees,like diplomats and intelligence officials who are stationed abroad. A senior administration official on Monday said that more than 50 US government personnel in 10 countries and 3 continents have been targeted by spyware in recent years.
In the constant cat-and-mouse game between spyware companies and those experts trying to stop the sophisticated technology from infecting phones, companies like Apple have notched up some victories. Researchers who study hacking have said that they have found evidence of individuals who use Apple’s “lockdown” security function of being targeted but not successfully infected by spyware.
Yet it remains a major issue, including in Jordan, where Access Now, an advocacy group, recently reported nearly three dozen cases of individuals who were targeted or hacked by Pegasus.
The state department said on Monday that the visa restrictions would also apply to individuals in countries that do not usually require a visa to enter the US, like EU countries and Israel. It is considered a “global” visa ban, so individuals who are potentially subject to the sanction would be notified that they are no longer eligible for visa-free travel and would need to apply for a visa at a US consulate if they are seeking to enter the US.
According to guidance issued by the state department, the ban will restrict entry for individuals believed to be involved in the misuse of commercial spyware “to target, arbitrarily or unlawfully surveil, harass, suppress, or intimidate individuals including journalists, activists, other persons perceived to be dissidents for their work, members of marginalized communities or vulnerable populations, or the family members of these targeted individuals”.
The visa ban will also affect individuals believed to facilitate or derive financial benefit from the misuse of commercial spyware and their immediate families. While the visa ban would not directly affect US financial firms or investors involved in the spyware industry, a senior administration official said that its actions would send an “important signal” about the risks associated with the industry.
Read More: https://www.theguardian.com/us-news/2024/feb/05/us-biden-administration-global-spyware-restrictions Source Credit: https://www.theguardian.com/
Opposition MP charged over alleged crimes when minister in former PiS government

New Android Malware NGate Steals NFC Data to Clone Contactless Payment Cards

Innovative Phishing Campaign Targets Mobile Users with PWAs
Geographic Reach and Victim Impact
The campaigns have extended their tentacles to target other regions, including Hungary and Georgia. Specifically, attacks were observed against OTP Bank in Hungary and a Georgian Bank. The cross-platform nature of PWAs enables the global reach of these campaigns, as the malicious app are able to operate on iOS and Android devices. ESET’s research also reveals that two distinct threat actors are behind these campaigns. However, the analysts discovered different Command and Control (C&C) infrastructures, suggesting that multiple groups are exploiting this novel phishing method.Delivery Mechanisms and Attack Flow
The campaigns use various methods to deliver phishing URLs, including automated voice calls, SMS messages, and malicious ads on social media platforms like Facebook and Instagram. These tactics lure users with tempting offers or warnings about outdated banking apps, leading them to download the phishing application. Once installed, the apps prompt users to enter their banking credentials, which are then transmitted to the attacker’ C&C servers. In some cases, stolen information is logged via Telegram bots, while other campaigns rely on traditional C&C servers with administrative panels.Mitigation Efforts
ESET has taken proactive steps to mitigate the impact of these phishing campaigns. By identifying and reporting compromised accounts, the company has worked with affected banks to protect customers. Additionally, ESET has been involved in the takedown of multiple phishing domains and C&C servers. This phishing method is a significant threat to mobile banking security. Its stealthy installation of PWAs and WebAPKs slips through traditional security nets, making it hard for users to recognize the danger. ESET analysts warn that more copycat applications could emerge in the coming months, posing a continued risk to mobile users worldwide. Read More:- https://informationsecuritybuzz.com/phishing-campaign-target-mobile-pwas/ Source Credit: https://informationsecuritybuzz.com/
This app hides in plain sight, records everything you do
LianSpy's stealthy operation and data theft
LianSpy was first detected in March 2024, but evidence suggests it has been operating covertly for at least three years.Unlike other spyware, this one requires user interaction to fully integrate into their device.Once activated, it asks for necessary permissions to use overlays, read contacts, and access call logs.If these permissions are not granted, LianSpy will request them from the user by masquerading as a system application or financial services app.
LianSpy's unique approach to data theft
Interestingly, LianSpy does not target banking information. Instead, it focuses on monitoring user activity on their Android device.The spyware is capable of stealing call logs, sending installed applications to its own servers, and recording a user's screen, without giving any clue to the user.It operates stealthily in the background using root privileges or superuser permissions that provide the highest level of access to an Android device.
LianSpy's evasion of Android security measures
When an app uses the phone's camera or microphone, an alert appears on the staus bar.However, LianSpy cleverly conceals its activity by exploiting root privileges to bypass the Android system's notification alerts.This means it can secretly record audio and video without any visible warning to the user.The spyware is a Trojan malware, meaning it can be delivered onto select Android devices via seemingly authentic files or apps like a software update, email attachment, or a scam app.
How to protect your Android device from spyware
To protect against spyware like LianSpy, users are advised to download apps only from official stores such as Play Store and websites.However, even these platforms can sometimes be infiltrated by malicious software.It's recommended that users only download necessary apps from trusted sources such as legitimate companies or brands.Regularly updating the device's operating systems is also crucial as malware often struggles to adapt to new security features and bug fixes.
Read More:- https://www.newsbytesapp.com/news/science/android-spyware-records-screen-steals-data-how-to-stay-safe/story Source Credit: https://www.newsbytesapp.com/
Digital rights NGO files complaints against European Parliament for data breach

Apple issues two fresh Pegasus-like spyware alerts in India
Iltija Mufti, political adviser and daughter of former Jammu and Kashmir chief minister Mehbooba Mufti, reported receiving the alert, and so did Pushparaj Deshpande, founder of the Samruddha Bharat Foundation
At least two people in India on July 10 reported receiving a Pegasus-like alert from Apple, Inc. on their iPhones. The alerts, sent out on Tuesday night, warn them that they have been targeted by a targeted “mercenary” attack. Apple previously called these attacks “state-backed,” but changed this in April. Such spyware allows attackers to sift through targets’ personal devices, allowing them to view messages, photos, and tap into microphone and camera feeds in real time.Pervious documented instances
This is the first time in months that such spyware alerts have been issued. The last documented instance during which individuals received alerts was last October, when Apple devices belonging to The Wire news portal’s founding editor Siddharth Varadarajan and Anand Mangnale, South Asia Editor at the Organised Crime and Corruption Report Project, received such alerts. Subsequent forensic testing showed they were targeted with a vulnerability used by Pegasus clients. Both Ms. Mufti and Mr. Deshpande blamed the Union government and insisted that the spyware they had been warned about was Pegasus. “BJP shamelessly snoops on women only because we refuse to toe their line,” Ms. Mufti said in a post on X, formerly Twitter. Mr. Deshpande said: “Countless problems facing India which GoI should be redressing. Instead it’s more focused in deploying #Pegasus to scare & suppress.” An international investigation in 2021 by the Forbidden Stories collective revealed the extent to which civil society organisations, opposition politicians and journalists were targeted around the world by Pegasus spyware. The Union government denied acting illegally but refused to confirm or deny expressly Pegasus deployment. Alleged targets revealed in 2021 include current Leader of the Opposition in the Lok Sabha Rahul Gandhi, former Election Commissioner Ashok Lavasa, student activist Umar Khalid, Union Minister Ashwini Vaishnaw, the entourage of the Dalai Lama, and the people charged in the Bhima Koregaon violence of 2018, including Stan Swamy, Shoma Sen and Rona Wilson. Read More:- https://www.thehindu.com/sci-tech/technology/apple-issues-two-fresh-pegasus-like-spyware-alerts-in-india/article68389054.ece Source Credit: https://www.thehindu.com/
Temu: The Trojan Horse in Your Pocket – A National Security Nightmare Unfolding
- Temu allegedly installs hidden spyware on your device, monitoring your every digital move.
- The app can reportedly override your privacy settings, access your camera, and even read your private messages.
- There are serious concerns that Temu products may be made with Uyghur slave labor, violating U.S. laws and contributing to one of the most egregious human rights abuses of our time.
- Congress must act immediately to ban Temu’s CCP forward operations in the United States.
- State governors and attorneys general across the nation should turn pressure into action. Ban Temu from state devices, continue to launch investigations, and use all means at your disposal to protect your citizens' data.
- Consumers, delete the app now! That $5 gadget isn't worth compromising your family’s personal information and aiding a foreign adversary.

Google to remove potentially risky app from Pixel devices following security report

Google Pixel phones found to have security flaws that control users’ data, report reveals
A significant security flaw found in Google Pixel phones could put millions of users' data at risk, according to a new report.
In Short
- The app 'Showcase.apk' preinstalled on Pixel phones can be exploited by hackers
- The app downloads information through an unsecure connection, making phones vulnerable
- Google has not yet provided a solution to fix this serious security issue

CYBERSECURITY experts have uncovered a mobile spyware application targeting Android smartphones.
- Replace or modify a device's operating system
- Install any apps, including specialized apps or apps not typically available on Android devices
- Customize the device, e.g. changing the home screen or using ad blockers

Poland launches inquiry into previous government’s spyware use
Poland has launched an investigation into its previous government’s use of the controversial spyware Pegasus, with a parliamentary inquiry under way and the possibility of criminal charges being brought against former government officials in future.
Adam Bodnar, Poland’s new justice minister, told the Guardian that in coming months the government would notify people who were targeted with Pegasus. Under Polish law, they would then have the possibility of seeking financial compensation, and becoming party to potential criminal proceedings.
“There is a decent chance that within a couple of months we’ll have quite extensive knowledge how this equipment was used and for what purpose,” said Bodnar.
On the possibility of future legal action, he added: “We don’t know who will be accused … if the investigation goes into the direction of accusing some persons, some ministers or officers of the security services.”
Pegasus is a powerful tool designed by Israeli company NSO Group. It is capable of taking control of a target’s mobile phone, accessing data from secure messaging apps and even turning the device into a recorder.
In 2021, a consortium of media outlets, including the Guardian, accessed a data leak that showed thousands of phone numbers that were targeted by Pegasus in various countries. It also revealed that the spyware tool had been used against media and civil society in numerous places, including in Hungary under the prime minister, Viktor Orbán.
Later that year, a separate investigation by the University of Toronto’s Citizen Lab revealed the use of Pegasus in Poland, including against targets linked to the Civic Platform party, then in opposition and now the main party in the governing coalition after parliamentary elections last October. The alleged targets included MEP Krzysztof Brejza, who at the time was running an election campaign for Civic Platform.
After the coalition, led by Civic Platform’s Donald Tusk, won Poland’s parliamentary elections last autumn, the new government promised to investigate alleged abuses of office by the rightwing nationalist Law and Justice (PiS) administration. The new authorities have replaced the management of state-controlled television, and set in train moves that could lead to the governor of the central bank, PiS ally Adam Glapiński, being removed from his post.
The parliamentary commission on Pegasus has begun amid widespread speculation of who else may have been targeted by the software. Magdalena Sroka, the MP heading the parliamentary commission, said after the first meeting of the panel: “Too long we’ve been lied to about Pegasus by PiS and we’re going to get to the bottom of it now.”
Bodnar – a lawyer and former human rights ombudsman appointed by Tusk as justice minister – said the full list remained confidential for now, but added that it included many more well-known peoplethan the few political figures already named. “This list is significantly more extensive than the list that has been made public already, a lot of other interesting public people,” he said.
Because Pegasus may also have been used in legitimate criminal investigations, it would be inappropriate simply to release a list of targeted numbers, said Bodnar. “You cannot just give away this data, even if the spyware is illegal,” he said.
Instead, the justice ministry and intelligence services plan to make a judgment on cases that appear to have been politicised or abusive and inform people individually by letter that they had been targeted. Then the person can make a decision themselves on whether to go public with the information or join in future legal action over the surveillance.
The legal side of the use of Pegasus also requires further investigation. Experts say that while court orders for surveillance were usually obtained, judges were not given full information about what exactly they were signing off on.
Bodnar said: “Apparently all those requests for using Pegasus had court authorisation, but most probably the courts didn’t know what kind of equipment would be used … They were authorising this but they did not know that [it involved] a programme that doesn’t have proper authorisation, and the data is going to Israel.”
Wojciech Klicki, a lawyer and activist with the Panoptykon Foundation, noted that judges would typically not even see the name of the person for whom they were approving a court order for surveillance.
“The system is constructed in a way that encourages judges to make automatic approvals of surveillance requests,” he said, during a recent panel discussion on the topic. “In the past couple of years the Warsaw district court saw a couple of dozen surveillance applications being submitted every day,” he added.
Polish authorities are believed to have stopped using Pegasus in 2021, around the time the Guardian and others publicised details of the spyware, including revelations that the numbers targeted by clients were also logged by NSO Group, creating a potential security breach.
The parliamentary inquiry is calling several key figures from the previous PiS government to give testimony, and has already taken testimony from PiS chairman Jarosław Kaczyński.
Klicki said that while it was important to uncover abuses of the past, he hoped the parliamentary commission would also tackle improving the legal framework long term. “It is equally important to look into the future … Otherwise we will forget that these technologies are evolving,” he said.
Additional reporting by Katarzyna Piasecka
Read More:- https://www.theguardian.com/world/2024/apr/01/poland-launches-inquiry-into-previous-governments-spyware-use Source Credit: https://www.theguardian.com/
MOE to remove Mobile Guardian app from students’ devices after global cybersecurity breach

Government alert for these Android users: Your phone may be prone to hacking
The vulnerability can allow hackers to “gain elevated privileges and obtain sensitive information on the targeted system”
The Indian Computer Emergency Response Team (CERT-In), which is a cybersecurity agency, warns Android users of facing cybersecurity issues. CERT-In explained that they have spotted high risk threats in Android versions prior 12, v12L, v13, and v14. The research team has already issued warnings of ‘high severity risk’ for people who are still using the above mentioned Android versions.CERT-In issues security alert
CERT-In explained that, if exploited, the vulnerability can allow hackers to “gain elevated privileges and obtain sensitive information on the targeted system”. This means that the affected users’ devices could be controlled by a hacker. They can then eventually access and steal sensitive information from a victim’s device. The cybersecurity agency further added that these vulnerabilities can exist in Android due to “flaws in the System, Google Play system updates, Framework, Kernel MediaTek components, Qualcomm components, Arm components, Imagination Technologies, and Qualcomm close-source components”. This means that if your device runs on Android versions prior to Android 12l, Android 12, Android 14, and Android 13, then you can face issues in the above-mentioned components. However, this is not the first time that CERT-In has issued warnings against security issues for smartphone users. Last year “Multiple vulnerabilities have been reported in Samsung products that could allow an attacker to bypass implemented security restrictions, access sensitive information, and execute arbitrary code on the targeted system,” CERT-In had said in a note.Safety road ahead
So, how can you protect your device? The CERT-In has come up with some guidelines that could protect you from this exploit. Given below are the steps through which you can protect yourself:- In case you suspect that your device has been compromised, always initiate a factory reset
- Next you should regularly back up your data to an external source or cloud service.
- Try to keep an eye on your device’s activity for any unusual behaviour. This could include sudden slowdowns, automated installation of unknown apps or unexpected pop-ups redirecting you links automatically
- You should try to avoid clicking on unknown links
- Always be cautious of unknown emails, messages or links, especially those that ask for personal information or credentials
- Use trusted sources: Only download apps from trusted sources like the Google Play Store.
- Try to consider installing reputable security software on your device.
- You need to regularly review the permissions that you have granted to your apps
- Lastly always go for automatic updates for both your apps and operating system

Security alert for Apple users: Govt issues ‘high risk’ advisory for several devices; check the full list

LianSpy is a new spyware that hides itself by blocking Android’s security feature
LianSpy can also turn off Android's Privacy Indicator, a feature that lets you know when your camera or microphone is in use.
Every month, Google releases security patches for Android that help block several malwares and spywares before they can damage your phone or tabletBut a new report by Kaspersky, the security firm that was recently banned in the United States recently discovered a spyware dubbed “LianSpy” that steals all your files, takes screenshots of what you are doing and even harvests call logs.Unlike most malwares that get detected in a couple of months, stealth techniques used by LianSpy have been so advanced that it remained undetected for over three years. According to Kaspersky, the malware poses itself as the Alipay app or a system service to evade detection.

Sophisticated Android Spyware Targets Users in Russia
An unknown — and likely state-sponsored — threat actor has been using a previously unseen mobile spyware tool to spy on an unknown number of Android smartphone users. This activity has been ongoing for at least three years, according to researchers.
Until now, the campaign has focused mainly on targeted individuals in Russia, according to researchers at Kaspersky, who are tracking the threat as LianSpy. But the tactics that the spyware operators used in deploying the malware could be easily applied in other regions as well, Kaspersky says.
Post-Exploit Malware
"LianSpy is a post-exploitation Trojan, meaning that the attackers either exploited vulnerabilities to root Android devices, or modified the firmware by gaining physical access to victims' devices," Kaspersky researcher Dmitry Kalinin wrote in a blog post this week. "It remains unclear which vulnerability the attackers might have exploited in the former scenario."
LianSpy is the latest in a fast-growing list of spyware tools. The list includes widely deployed products such as the NSO Group's Pegasus Software and the Intellexa alliance's Predator. Researchers have discovered these malware instances targeting iPhone and Android smartphone users in recent years. The main purchasers — and users — of these tools are typically governments and intelligence agencies that want to spy on dissidents, political opponents and other persons of interest to them.
In many instances — as was the case with last year's Operation Triangulation iOS spyware campaign — the purveyors of mobile spyware tools have exploited zero-day flaws in Android and iOS to deliver and/or run their malware on target devices. In other instances, including one involving an Android spyware tool dubbed BadBazaar last year and another espionage tool dubbed SandStrike in 2022, threat actors have distributed spyware via fake versions of popular applications on official mobile app stores.
A Three Year Campaign
Kaspersky researchers first stumbled on LianSpy in March 2024 and quickly determined that the entity behind it has been using the spyware tool since July 2021. Their analysis reveals that the attackers are likely distributing the malware disguised as systems applications and financial applications.
Unlike some so-called zero-click spyware tools, LianSpy's ability to function depends, to a certain extent, on user interaction. When launched, the malware first checks to see if it has the required permissions to execute its mission on the victim's device. If it does not have the required permissions, the malware prompts the user to provide them. When LianSpy obtains permission, it registers what is known as an Android Broadcast Receiver to receive and respond to system events such as booting, low battery, and network changes. Kaspersky researchers found LianSpy is using super user binary with a modified name ("mu" instead of "su") to try and gain root access on a victim device. Kaspersky officials say this as an indication that the threat actor delivered the malware after first gaining access to the device another way.
"Upon launch, the malware hides its icon on the home screen and operates in the background using root privileges," Kalinin wrote. "This allows it to bypass Android status bar notifications, which would typically alert the victim that the smartphone is actively using the camera or microphone."
Data Harvesting and Exfiltration
LianSpy's primary function is to quietly monitor user activity by intercepting call logs, recording the device screen especially when the user is sending or receiving messages and enumerating all installed apps on the victim device. The threat actor behind the malware has not used private infrastructure for communicating with the malware or storing harvested data. Instead, the attacker has been using public cloud platforms and pastebin services for these functions.
"The threat actor leverages Yandex Disk for both exfiltrating stolen data and storing configuration commands. Victim data is uploaded into a separate Yandex Disk folder," Kaspersky said in a technical writeup on the malware.
One interesting aspect about LianSpy, according to Kaspersky, is how the malware uses its root privileges on a compromised device. Instead of using its superuser status to take complete control of a device, LianSpy uses just enough of the functionality available to carry out its mission in a quiet fashion. "Interestingly, root privileges are used so as to prevent their detection by security solutions," the security vendor says. Kaspersky researchers also found LianSpy to be using both symmetric and asymmetric keys for encrypting the data it exfiltrates, which makes victim identification impossible.
"Beyond standard espionage tactics like harvesting call logs and app lists, it leverages root privileges for covert screen recording and evasion," Kalinin said. "Unlike financially motivated spyware, LianSpy's focus on capturing instant message content indicates a targeted data-gathering operation."
Read More:- https://www.darkreading.com/mobile-security/sophisticated-android-spyware-targets-users-in-russia
Source Credit: https://www.darkreading.com/
Mass app deletion coming to Android phones imminently
Tech giant Google is about to purge some of the most annoying — and dangerous apps from its popular Play Store.

New BingoMod Android Malware Posing as Security Apps, Wipes Data

Malware attacks in India increase by 11%; 22% jump seen in ransomware

Probe clears Greek government agencies in spyware scandal but opposition calls it a cover-up
ATHENS, Greece -- A two-year investigation in Greece has cleared the country’s security agencies of involvement in an international spyware scandal that triggered sanctions by the United States earlier this year, a senior prosecutor said Tuesday.
Supreme Court prosecutor Georgia Adilini said she found no evidence linking Greece’s National Intelligence Service, the police force or its anti-terrorism division to the use of Predator spyware, which opposition groups alleged was used against some government critics.
The spyware targeted dozens of prominent individuals in Greece including Nikos Androulakis, the current leader of a Socialist party, the third largest in parliament.
The investigation's findings drew an angry reaction from left-wing and center-left opposition parties in Greece which accused the ruling conservatives of engineering a cover-up.
Speaking in parliament, Androulakis called the investigation a “sham” and demanded that lawmakers be shown full conclusions of the probe, detailed in a 300-page report that has not been made public.
“It’s a shameful practice to sell this type of software to illiberal regimes, knowing that they are most likely to be used against human rights (activists), against political opponents, and endangering the lives of thousands of people in third world countries,” Androulakis said.
In March, the U.S. Treasury Department imposed sanctions against two individuals and companies based in Greece, Ireland, Hungary and North Macedonia, all connected to software developers called the Intellexa consortium.
The sanctions announcement said they were linked to the spyware that was being sold to authoritarian regimes around the world and being used to target U.S. citizens.
The government said its opponents had baselessly conflated the use of spyware with legally authorized wiretaps carried out by Greece’s National Intelligence Service.
“Your political narrative was not served by the facts. What should we do?,” Makis Voridis, a minister of state for the government, told parliament.
“While you were hurling slander, lies, and falsehoods at us – with nothing based on facts or the law – we were waiting for justice. And today, that day arrived.”
U.S. authorities say Predator spyware can infect electronic devices through so-called “zero-click attacks,” requiring no user interaction. Once infected, it enables secret data extraction, geolocation tracking, and access to applications and personal information.
Amnesty International’s Security Lab in October last year published a report that said that Predator had been used to target but not necessarily infect devices connected to the president of the European Parliament, Roberta Metsola, and the president of Taiwan, Tsai Ing-Wen, as well as Rep. Michael McCaul, R-Texas, and Sen. John Hoeven, R-N.D.
The alleged use of Predator spyware in Greece helped precipitate the resignation in 2022 of two top government officials, including the national intelligence director.
Greek lawmakers in late 2022, passed legislation to ban the use, sale or distribution of the spyware, with violations carrying a penalty of a two-year minimum prison sentence.
Read More:- https://abcnews.go.com/US/wireStory/probe-clears-greek-government-agencies-spyware-scandal-opposition-112416341 Source Credit: https://abcnews.go.com/US/wireStory
Android spyware ‘Mandrake’ hidden in apps on Google Play since 2022
- AirFS – File sharing via Wi-Fi by it9042 (30,305 downloads between April 28, 2022, and March 15, 2024)
- Astro Explorer by shevabad (718 downloads from May 30, 2022 to to June 6, 2023)
- Amber by kodaslda (19 downloads between February 27, 2022, and August 19, 2023)
- CryptoPulsing by shevabad (790 downloads from November 2, 2022, to June 6, 2023)
- Brain Matrix by kodaslda (259 downloads between April 27, 2022 and June 6, 2023)
Upon the malicious app's installation, the library exports functions to decrypt the second-stage loader DEX from its assets folder and load it into memory.
The second stage requests permissions to draw overlays and loads a second native library, 'libopencv_java3.so,' which decrypts a certificate for secure communications with the command and control (C2) server. Having established communication with the C2, the app sends a device profile and receives the core Mandrake component (third stage) if deemed suitable. Once the core component is activated, Mandrake spyware can perform a wide range of malicious activities, including data collection, screen recording and monitoring, command execution, simulation of user swipes and taps, file management, and app installation. Notably, the threat actors can prompt users to install further malicious APKs by displaying notifications that mimic Google Play, hoping to trick users into installing unsafe files through a seemingly trusty process. Kaspersky says the malware also uses the session-based installation method to bypass Android 13's (and later) restrictions on the installation of APKs from unofficial sources. Like other Android malware, Mandrake can ask the user to grant permission to run in the background and hide the dropper app's icon on the victim's device, operating stealthily. The malware's latest version also features batter evasion, now specifically checking for the presence of Frida, a dynamic instrumentation toolkit popular among security analysts.It also checks the device root status, searches for specific binaries associated with it, verifies if the system partition is mounted as read-only, and checks if development settings and ADB are enabled on the device.
The Mandrake threat remains alive, and while the five apps identified as droppers by Kaspersky are no longer available on Google Play, the malware could return via new, harder-to-detect apps. Android users are recommended only to install apps from reputable publishers, check user comments before installing, avoid granting requests for risky permissions that seem unrelated to an app's function, and make sure that Play Protect is always active. Google shared the following statement about the malicious apps found on Google Play. "Google Play Protect is continuously improving with each app identified. We're always enhancing its capabilities, including upcoming live threat detection to help combat obfuscation and anti-evasion techniques," Google told BleepingComputer. "Android users are automatically protected against known versions of this malware by Google Play Protect, which is on by default on Android devices with Google Play Services. Google Play Protect can warn users or block apps known to exhibit malicious behavior, even when those apps come from sources outside of Play." Read More:- https://www.bleepingcomputer.com/news/security/android-spyware-mandrake-hidden-in-apps-on-google-play-since-2022/ Source Credit: https://www.bleepingcomputer.com/news/security/
Raghav Chadha asks Centre to investigate spyware attacks on politicians and journalists in Rajya Sabha
Raghav Chadha said that not just the members of Parliament but journalists and eminent people were also victims of such attack.
The Aam Aadmi Party’s Rajya Sabha MP Raghav Chadha on Friday raised the issue of State-sponsored cyberattacks on politicians and journalists in the House and asked the Centre to investigate such attacks. Calling it an attack on privacy, Mr. Chadha said that several opposition leaders had last year claimed they received an alert from Apple warning them of “State-sponsored attackers trying to remotely compromise”. He asked the government if it had taken cognisance of such attacks. “I, along with several members of this House, particularly who sit on opposition benches, were victims of something called State-sponsored spyware attack whereby our mobile phones informed us that a State-sponsored cyberattack took place which was attempting to infiltrate our mobile phone devices,” Mr. Chadha said. He said that not just the members of Parliament but journalists and eminent people were also victims of such attack. “Therefore, I ask you whether the government has taken cognisance of such attacks. Is there a list of people who were attacked by such spyware. What action has been taken?” Mr. Chadha asked. Read More:- https://www.thehindu.com/news/national/raghav-chadha-asks-centre-to-investigate-spyware-attacks-on-politicians-and-journalists-in-rajya-sabha/article68451497.ece Source Credit: https://www.thehindu.com/news/national
Candiru: New spyware attack on member of European Parliament
Growing evidence that the Indian State bought Pegasus spyware, the technical committee told
While the Govt of India has neither confirmed nor denied that it bought the spyware, in his deposition a cyber security expert has claimed there are definite traces of use by govt agencies

Tech giants say spyware victims should be able to sue NSO Group in US
Microsoft, Google and several other major tech firms on Monday filed a legal brief supporting an El Salvadoran journalist whose staff was targeted with powerful mobile spyware, arguing he should be allowed to sue the software developer in U.S. court.
In March, a California federal judge dismissed the lawsuit brought by Carios Dada and other plaintiffs located overseas against Israeli spyware maker NSO Group, saying they had no standing to sue in the United States because the case was “entirely foreign.”
The amicus brief argues that Google, Microsoft and other U.S. technology companies supporting the plaintiffs have worked closely with policymakers to enhance cybersecurity and collectively spend billions annually to bolster it, partially by working to monitor and disrupt spyware.
The dismissal is now being appealed, apparently spurring the technology companies’ brief asserting that they have a “strong interest in ensuring that entities who facilitate covert access to their products are held accountable in U.S. courts.”
“Even if NSO’s spyware tools were not being used to target U.S. citizens and officials, the proliferation of these tools would still inflict substantial harm on important U.S. interests,” the brief said, noting that the spyware undermines customers’ faith in their products and threatens national security.
The plaintiffs had asked the judge to force NSO Group to return and erase all information accessed through the hacks and name the clients which sought the Pegasus spyware used in them.
Pegasus targets thousands in civil societyDada co-founded and directs the Salvadoran news outlet El Faro, which was investigating its government’s hidden ties to violent gangs when his and several staffers’ phones were infected with the zero-click Pegasus spyware.
Pegasus is manufactured by NSO and was allegedly installed on the phones of 22 El Faro employees between June 2020 and November 2021, according to digital forensic researchers.
The lawsuit, the first filed by journalists against the spyware manufacturer in a U.S. court, centers on the fact that El Faro staffers’ phones were allegedly hit with 226 Pegasus infections.between June 2020 and November 2021, according to the Knight First Amendment Institute at Columbia University, which brought the case.
NSO Group is also currently being sued by Meta-owned WhatsApp, which asserts about 1,400 of its users also were hacked by Pegasus and that U.S.-based Amazon Web Services unknowingly stored Pegasus code for years.
In addition to Google and Microsoft, GitHub, LinkedIn and Trend Micro joined in filing the amicus brief supporting the lawsuit’s plaintiffs as their appeal of the dismissal unfolds.
The brief cites a July 2021 Amnesty International and Forbidden Stories investigation known as the Pegasus Project, which published more than 50,000 phone numbers found in a leaked database. Some of the numbers were thought to have been hacked with Pegasus.
The organizations found phone numbers belonging to 14 heads of state — including from France, Iraq, Morocco, Pakistan and Egypt — along with 600 government officials and more than 180 journalists in the database, the brief said. Pegasus can only be installed if attackers possess a given target’s phone number.
A majority of phones analyzed as part of a study of a relatively small subset of the database‘s list of numbers contained evidence of Pegasus spyware, the brief noted.
“NSO admits to having sold Pegasus to approximately 40 different governments around the world,” the brief said, noting that the company claims it works hard to vet its clients for human rights abuses in part by only allowing its spyware to be used only by law enforcement and intelligence agencies, primarily in counterterrorism efforts.
However, the brief noted, the fact that the database included targets with no connection to crime or terrorism, also including executives, religious leaders and academics, show “these protections — if they ever existed — have failed to prevent abuse.”
“It appears that, once a government purchased Pegasus from NSO, it could use the tool to hack and spy on whomever it wanted,” the brief added.
Google and Microsoft’s motivesMicrosoft explained its reasons for filing the brief on a website blog penned by its associate general counsel for cybersecurity policy and protection, who said the company has long demonstrated its belief that cyber mercenaries such as NSO Group “don’t deserve immunity.”
“Despite measures taken by governments, regulators, and tech companies, the impact of these actors on the security of users continues to increase as the market expands,” the blog post said. “More must be done.”
NSO Group has consistently used Microsoft technology to attack its users, the blog post added, arguing that those users deserve “legal recourse” even if they are located abroad.
Google’s heads of security policy and security legal also published a blog post Monday, saying that while spyware usually only impacts a small number of users, “its wider impact ripples across society by contributing to threats to free speech, the free press and the integrity of elections worldwide.”
Many victims of spyware hacks use U.S.-based platforms such as Android or iOS from abroad, the post said.
“Our filing argues that victims of spyware-enabled attacks should be able to take legal action in the U.S. against spyware vendors under existing anti-hacking laws — even if they were hacked abroad,” the post said. “This is imperative to narrow the attack vectors exploited by spyware vendors.”
Read More:- https://therecord.media/microsoft-google-amicus-brief-nso-group-lawsuit Source Credit: therecord.media
Khashoggi’s widow sues Israeli spyware company NSO over phone hacking

Pro-Houthi Group Targets Yemen Aid Organizations with Android Spyware
ISOC denies using Israeli Pegasus spyware to track Thai activists
The Internal Security Operations Command (ISOC) on Thursday denied that it had ever used the Pegasus spyware of Israel's NSO Group to steal information and track the mobile phones of Thai activists.

MP Congress chief files complaint over ‘spyware attack on his iPhone’
This comes days after Congress General Secretary K C Venugopal accused the Narendra Modi-led central government of using a “malicious spyware” to try and hack his mobile phone.
Madhya Pradesh State Congress chief Jitu Patwari claimed that his iPhone was targeted by “spyware which was a state-sponsored attempt to misuse his data for political gains”.Patwari filed a complaint with the Additional DGP Cyber Cell office in Bhopal, alleging that on July 9 he received a threat notification on his email ID and another on July 11 about an account recovery request for his Apple ID.

Predator Spyware Is Alive & Well & Expanding
Mercenary spyware operator has rebuilt its network infrastructure and now operates in 11 countries, with one of the newest additions, Botswana.
The infamous Predator mobile spyware operation publicly exposed in an eye-popping report last year by Amnesty International has revamped its malware delivery network and expanded its reach into Botswana and the Philippines.
Researchers from Recorded Future's Insikt Group, which spotted Predator's updated architecture, said the mercenary mobile spyware enterprise now operates in at least 11 countries with the addition of Botswana and the Philippines.
The updated and tiered malware network infrastructure includes delivery servers, upstream servers, and static IP addresses in the 11 nations suspected to be Predator customers: Angola, Armenia, Botswana, Egypt, Indonesia, Kazakhstan, Mongolia, Oman, the Philippines, Saudi Arabia, and Trinidad and Tobago.
"While Predator stands out as one of the premier providers of mercenary spyware, alongside NSO Group's Pegasus, the tactics, techniques, and procedures [TTPs] it uses during its delivery process have remained consistent over time, likely indicating their ongoing success," the Insikt team wrote in its findings.
Read More:- https://www.darkreading.com/remote-workforce/predator-mobile-spyware-alive-and-well-and-expanding
Source Credit: https://www.darkreading.com/

Govt using ‘spyware’ to target my phone, says Venugopal
Venugopal shared the screenshot of a message purportedly from Apple, which read, "You are being targeted by a mercenary spyware attack that is trying to remotely compromise the iPhone associated with your Apple ID."
Congress MP and General Secretary in-charge of organisation KC Venugopal Saturday accused the “Modi government of using a malicious spyware” to target his mobile phone and said “we will oppose this blatantly unconstitutional act and breach on our privacy tooth and nail”.He said the attack came to his attention after Apple sent him an alert.

Data breach exposes millions of mSpy spyware customers
Customer service emails dating back to 2014 exposed in May breach
A data breach at the phone surveillance operation mSpy has exposed millions of its customers who bought access to the phone spyware app over the past decade, as well as the Ukrainian company behind it.
Unknown attackers stole millions of customer support tickets, including personal information, emails to support, and attachments, including personal documents, from mSpy in May 2024. While hacks of spyware purveyors are becoming increasingly common, they remain notable because of the highly sensitive personal information often included in the data, in this case about the customers who use the service.
The mSpy app allows whoever planted the spyware, typically someone who previously had physical access to a victim’s phone, to remotely view the phone’s contents in real-time.
As is common with phone spyware, mSpy’s customer records include emails from people seeking help to surreptitiously track the phones of their partners, relatives, or children, according to TechCrunch’s review of the data, which we independently obtained. Some of those emails and messages include requests for customer support from several senior-ranking U.S. military personnel, a serving U.S. federal appeals court judge, a U.S. government department’s watchdog, and an Arkansas county sheriff’s office seeking a free license to trial the app.
Even after amassing several million customer service tickets, the leaked Zendesk data is thought to represent only the portion of mSpy’s overall customer base who reached out for customer support. The number of mSpy customers is likely to be far higher.
Yet more than a month after the breach, mSpy’s owners, a Ukraine-based company called Brainstack, have not acknowledged or publicly disclosed the breach.
Hunt told TechCrunch that he contacted several Have I Been Pwned subscribers with information from the breached data, who confirmed to him that the leaked data was accurate.
Millions of mSpy customer messages
TechCrunch analyzed the leaked dataset — more than 100 gigabytes of Zendesk records — which contained millions of individual customer service tickets and their corresponding email addresses, as well as the contents of those emails.
Some of the email addresses belong to unwitting victims who were targeted by an mSpy customer. The data also shows that some journalists contacted the company for comment following the company’s last known breach in 2018. And, on several occasions, U.S. law enforcement agents filed or sought to file subpoenas and legal demands with mSpy. In one case following a brief email exchange, an mSpy representative provided the billing and address information about an mSpy customer — an alleged criminal suspect in a kidnapping and homicide case — to an FBI agent.
TechCrunch analyzed where mSpy’s contacting customers were located by extracting all of the location coordinates from the dataset and plotting the data in an offline mapping tool. The results show that mSpy’s customers are located all over the world, with large clusters across Europe, India, Japan, South America, the United Kingdom, and the United States.
Buying spyware is not itself illegal, but selling or using spyware for snooping on someone without their consent is unlawful. U.S. prosecutors have charged spyware makers in the past, and federal authorities and state watchdogs have banned spyware companies from the surveillance industry, citing the cybersecurity and privacy risks that the spyware creates. Customers who plant spyware can also face prosecution for violating wiretapping laws.
According to the data, one of the email addresses pertains to Kevin Newsom, a serving appellate judge for the U.S. Court of Appeals for the Eleventh Circuit across Alabama, Georgia, and Florida, who used his official government email to request a refund from mSpy.
The dataset also shows interest from U.S. authorities and law enforcement. An email from a staffer at the Office of the Inspector General for the Social Security Administration, a watchdog tasked with oversight of the federal agency, asked an mSpy representative if the watchdog could “utilize [mSpy] with some of our criminal investigations,” without specifying how.
The Arkansas County sheriff’s department sought free trials of mSpy, ostensibly for providing demos of the software to neighborhood parents. That sergeant did not respond to TechCrunch’s question about whether they were authorized to contact mSpy.
The company behind mSpy
This is the third known mSpy data breach since the company began in around 2010. mSpy is one of the longest-running phone spyware operations, which is in part how it accumulated so many customers.
But the data breach of mSpy’s Zendesk data exposed its parent company as a Ukrainian tech company called Brainstack.
Brainstack’s website does not mention mSpy. Much like its public open job postings, Brainstack only refers to its work on an unspecified “parental control” app. But the internal Zendesk data dump shows Brainstack is extensively and intimately involved in mSpy’s operations.
In the leaked Zendesk data, TechCrunch found records containing information about dozens of employees with Brainstack email addresses. Many of these employees were involved with mSpy customer support, such as responding to customer questions and requests for refunds.
Brainstack chief executive Volodymyr Sitnikov and senior executive Kateryna Yurchuk did not respond to multiple emails requesting comment prior to publication. Instead, a Brainstack representative, who did not provide their name, did not dispute our reporting but declined to provide answers to a list of questions for the company’s executives.
It’s not clear how mSpy’s Zendesk instance was compromised or by whom. The breach was first disclosed by Switzerland-based hacker maia arson crimew, and the data was subsequently made available to DDoSecrets, a nonprofit transparency collective that indexes leaked datasets in the public interest.
“We are committed to upholding our User Content and Conduct Policy and investigate allegations of violations appropriately and in accordance with our established procedures,” the spokesperson said.
Read More:- https://techcrunch.com/2024/07/11/mspy-spyware-millions-customers-data-breach/ Source Credit: https://techcrunch.com/2024/07/11
Apple warns iPhone users in India, 97 other countries of Pegasus-like spyware attack
Apple has once again notified users that their iPhone may have been affected by a potential mercenary spyware like Pegasus.
Apple has once again issued a new round of warnings for iPhone users in 98 countries including India, warning them that they might potentially be targeted by a Pegasus like spyware. Earlier this year in April, the Cupertino-based tech giant sent a similar notification to users across 92 nations.According to a support document on the Apple website, the company has been regularly informing iPhone users across 150 countries worldwide about these types of attacks. However, the latest notification did not disclose the attacker’s identities and the list of countries where users received the alert.

Brussels spyware bombshell: Surveillance software found on officials’ phones

CapraRAT malware targeting Android users with fake apps

U.S. bans maker of spyware that targeted a senator’s phone
The Treasury Department on Tuesday banned a notorious creator of software that can hack smartphones and turn them into surveillance devices from doing business in the U.S.
The sanctions constitute the most aggressive action taken by the U.S. government against a spyware company.
The company, Intellexa, develops a software called Predator, which can take over a person’s phone and turn it into a surveillance device. Predator and other major spyware programs boast capabilities such as secretly turning on the user’s microphone and camera, downloading their files without their knowledge and tracking their location.
Under the sanctions, Americans and people who do business with the U.S. are forbidden from transacting with Intellexa, its founder and architect Tal Dilian, employee Sara Hamou and four companies affiliated with Intellexa.
In a press call previewing the sanctions, a White House official, who requested to not be identified, said the decision to sanction Intellexa “goes beyond actions we’ve taken.”
“This is the first time that the U.S. government has leveraged any sanctions authority against commercial spyware vendors for enabling misuse of their tools,” he said.
An Amnesty International investigation found that Predator has been used to target journalists, human rights workers and some high-level political figures, including European Parliament President Roberta Metsola and Taiwan’s outgoing president, Tsai Ing-Wen. The report found that Predator was also deployed against at least two sitting members of Congress, Rep. Michael McCaul, R-Texas, and Sen. John Hoeven, R-N.D.
Predator was also central to a scandal that rocked Greece in 2022 in which dozens of politicians and journalists were reportedly targeted with the spyware.
NBC News was unable to reach Intellexa for comment. Its website has been offline since sometime in 2023.
Multiple governments around the world “have deployed this technology to facilitate repression and enable human rights abuses, including to intimidate political opponents and curb dissent, limit freedom of expression, and monitor and target activists and journalists,” a Treasury Department press release on the sanctions said.
The sanctions follow President Joe Biden’s 2023 executive order regulating commercial spyware.
Under that order, the Commerce Department previously placed another spyware developer, the Israeli company NSO Group, on the U.S. entity list, subjecting it to additional regulations. But sanctioning Intellexa is an escalation, said John Scott-Railton, a senior spyware researcher at the University of Toronto’s Citizen Lab.
“The U.S. using Treasury sanctions is going to be a thunderclap for the spyware world,” he said. “Suddenly this has big, personal consequences.”
“This is the kind of stuff that causes people to consider changing lines of work and leaving countries,” he said.
Read More:- https://www.nbcnews.com/tech/security/us-bans-maker-spyware-targeted-senators-phone-rcna141855 Source Credit: https://www.nbcnews.com/tech/security/
Indian journalist’s phone targeted with Israeli spyware Pegasus: Report
The forensic work on Magnale's phone found a pattern of suspicious crashes on it that matched previously known Pegasus intrusions.
An Indian journalist has been allegedly subjected to hacking using Pegasus, a spyware manufactured by Israel-based NSO Group. An analysis of the journalist's iPhone showed an infiltration attempt was made in August, news agency Reuters reported. Anand Magnale, who works for a global group of investigative journalists called Organised Crime and Corruption Reporting Project (OCCRP), was reportedly among those in India who received alerts on their Apple mobile devices which prompted a row over issue of national security and call for stringent IT rules. Several politicians were also among those who received the Apple alerts, who claimed that they have been targetted by ‘state-sponsored’ hackers in order to remotely access their iPhones. However, those alerts didn't specify any government entity behind the hacks or any use of spyware. Moreover, the Indian government has also dismissed the allegations of being involved in the ‘hacking’ alerts and ordered an inquiry into the matter. OCCRP co-founder Drew Sullivan told the news agency that the forensic work on Magnale's phone found a pattern of suspicious crashes on it that matched previously known Pegasus intrusions. The journalist hasn't responded on the matter. The Union IT ministry also didn't react to the report immediately. Pegasus, sold exclusively to government bodies, manufactured to combat terror and crime which works by allowing sweeping access to the targets' smartphones, allowing them to record calls, intercept messages and transform the phones into portable listening devices. "Whatever government is spying on the reporters, there's no plausible explanation for that other than political gain," Sullivan told Reuters. iVerify, the company that ran the forensics on Magnale's phone said ‘with high confidence’ that his phone was attacked with Pegasus. Read More:- https://www.hindustantimes.com/india-news/indian-journalists-phone-targetted-with-israeli-spyware-pegasus-report-101699501184036.html Source Credit: https://www.hindustantimes.com/
Government and military officials fair targets of Pegasus spyware in all cases, NSO Group argues
The manufacturers of the powerful commercial spyware Pegasus argued in a Friday court filing that it is appropriate for its global clients to target any high-ranking government or military official with the technology because their jobs categorically make them “legitimate intelligence targets.”
The statement is a revelatory admission from the typically tight-lipped Pegasus manufacturer, NSO Group, regarding who it believes can justifiably be targeted with its zero-click and all-seeing surveillance product.
It surfaced in court documents related to a lawsuit WhatsApp has brought against NSO Group for allegedly infecting about 1,400 of its users’ devices with the technology. The hacks were discovered in 2019.
A former United Nations official overseeing the right to free expression said NSO Group’s comments go beyond their prior assertions and are more sweeping in their definition of who can legitimately be targeted by Pegasus.
The official, David Kaye, pointed to a 2019 NSO Group letter sent to him while he was at the U.N. It said Pegasus is “intended to prevent acts of terrorism, large-scale drug trafficking, pedophile networks, and other serious criminal acts.”
In that same letter, NSO Group said that its contracts with clients “specifically demand that customers utilize our technologies as intended – to investigate and prevent crimes and terrorism.”
Friday’s filing seems to suggest a broader purpose for Pegasus, Kaye said, pointing to NSO’s explanation that the technology can be used on “persons who, by virtue of their positions in government or military organizations, are the subject of legitimate intelligence investigations.”
“This appears to be a much more extensive claim than made in 2019, since it suggests that certain persons are legitimate targets of Pegasus without a link to the purpose for the spyware’s use,” said Kaye, who was the U.N.’s special rapporteur on freedom of opinion and expression from 2014 to 2020.
NSO Group clients include or have included repressive regimes such as Hungary, the United Arab Emirates and Saudi Arabia. Pegasus technology was allegedly used to track journalist Jamal Khashoggi in the months before he was murdered by the Saudi government.
The Israeli company’s statement comes as digital forensic researchers are increasingly finding Pegasus infections on phones belonging to activists, opposition politicians and journalists in a host of countries worldwide.
NSO Group says it only sells Pegasus to governments, but the frequent and years-long discoveries of the surveillance technology on civil society phones have sparked a public uproar and led the U.S. government to crack down on the company and commercial spyware manufacturers in general.
Debating legitimate Pegasus targets
Friday’s court filing centers on a fight between NSO Group, WhatsApp and digital forensic researchers from The Citizen Lab, whose experts helped research many of the Pegasus infections documented in the case.
NSO Group wants The Citizen Lab to turn over information about additional victim identities and how it made its analysis.
The debate focuses on lists The Citizen Lab produced classifying Pegasus infections as affecting either top government and military officials — referred to in the filing as the VIP list — or civil society leaders.
NSO says the list of individuals The Citizen Lab classified as VIPs includes 93 people the company describes as “high-ranking government or military officials.”
“The VIP list is almost entirely comprised of persons who, by virtue of their positions in government or military organizations, are the subject of legitimate intelligence investigations,” an attorney for NSO Group wrote in the filing. “All the VIPs are legitimate intelligence targets.”
The company accessed the lists through discovery because The Citizen Lab worked with WhatsApp to help identify and alert civil society victims when the hacks were first found in 2019. Not all of the approximately 1,400 total victims are identified or classified in the lists obtained by NSO Group, which is seeking the additional names and classifications.
An NSO Group spokesperson could not immediately be reached for comment on this story, but told Recorded Future News last week that it “complies with all laws and regulations and sells only to vetted intelligence and law enforcement agencies.”
“Our customers use these technologies daily to prevent crime and terror attacks,” they said.
The company does not disclose its client list, but the spokesperson noted it doesn’t work with Russia or its allies.
Opposition ‘VIPs’
NSO Group also appeared to suggest in court filings that opposition politicians can be legitimately surveilled with Pegasus. This assertion comes as Polish officials investigate what they have described as a Pegasus-enabled coordinated campaign by the country’s former majority to track hundreds of opposition party politicians and those aligned with them.
“Citizen Lab appears to have drawn a distinction between politicians whose parties are in power (VIPs) versus politicians belonging to opposition parties (civil society),” the NSO Group lawyer wrote.
“For purposes of determining whether an individual was legitimately surveilled (eg, as part of an intelligence operation) using Pegasus, defendants submit that this distinction is unjustified and all senior political operatives should be classified as VIPs.”
Poland is far from the only country where Pegasus has targeted minority party officials and civil society leaders. In 2022, The Citizen Lab published a report documenting that Pegasus was used to target at least 63 Catalan government officials and activists following a 2017 bid for independence.
A spate of Pegasus infections targeting Indian journalists — whose most recent victims were made public in December by Amnesty International — is also cited by the NSO lawyer, who said that a “supposed” Indian journalist included on The Citizen Lab’s list was sentenced to life imprisonment for “sedition and waging war against the nation.”
Calling the journalist and some others The Citizen Lab classified as civil society victims “criminals,” the lawyer suggests their inclusion on the list shows The Citizen Lab has “hugely overreached… in an effort to further its agenda that the use of Pegasus against civil society targets is widespread.”
The Indian government was found to have bought Pegasus from Israel in 2017. Multiple news reports have suggested that Indian Prime Minister Narendra Modi's government has used Pegasus to spy on and potentially even jail its critics.
A forensic analysis of a device belonging to imprisoned Indian activist and Modi critic Rona Wilson found evidence that it was infected with Pegasus between 2017 and March 2018. In June 2018 Wilson was arrested on terror-related charges.
'Lawfully targeted'
The Citizen Lab lawyer argued in the filing that NSO Group has no standing to compel it to turn over information on Pegasus targets or its analysis.
NSO Group is seeking a so-called letter rogatory to force disclosures from The Citizen Lab.
Letters rogatory are typically used to obtain evidence if permitted by the laws of the foreign country involved in a lawsuit. NSO Group is based in Israel, The Citizen Lab in Canada and Meta, which owns WhatsApp, is in the U.S.
“The core rationale for defendants’ request — their disagreement with The Citizen Lab’s categorization of listed individuals — is irrelevant,” the digital freedom research institute’s lawyer asserts.
In order to compel material from The Citizen Lab, NSO Group’s defense must show that individuals were “lawfully targeted by a U.S. law enforcement or intelligence agency,” the lawyer asserted.
The Citizen Lab did not respond to a request for comment.
A spokesperson for WhatsApp pointed to the company’s comments to the judge in the Friday filing, emphasizing that NSO Group relied only on public information from “questionable or biased sources” in challenging The Citizen Lab classifications of victims.
NSO Group illegally targeted WhatsApp’s systems and users with their spyware, “a pattern of abuse that cannot be tolerated by liberal democracies,” the spokesperson said via email.
In March, a California federal judge ordered NSO Group to turn over its closely guarded secret code as part of discovery in the years-long lawsuit, a decision seen as a major win for WhatsApp.
Read More:- https://therecord.media/government-military-fair-targets-nso-group Source Credit: https://therecord.media/
LightSpy Spyware Campaign Targets iPhones Across South Asia
- iPhone users across South Asian countries face a new spyware campaign threat called LightSpy.
- The spyware implant creates an advanced backdoor in iOS that is usually distributed through compromised websites and watering hole attacks.

Poland’s right-wing leader questioned over Pegasus spyware
The Law and Justice (PiS) party, which ruled Poland from 2015 to 2023, is suspected of having spied on opposition politicians and magistrates critical of its administration
The chairman of Poland’s main populist party Jaroslaw Kaczynski appeared before a parliamentary commission on Friday over the alleged use of the Israeli spyware Pegasus while it led the country’s previous government. The Law and Justice (PiS) party, which ruled from 2015 to 2023, is suspected of having spied on opposition politicians and magistrates critical of its administration. Mr. Kaczynski, who also served as Poland’s Prime Minister, acknowledged in 2022 that his country had bought the spyware but denied that it had been used against critics. Ahead of Friday’s inquiry, the head of the commission, Magdalena Sroka, said Mr. Kaczynski was picked first to testify because of his “responsibility for the actions of the Law and Justice Party, which was in power until 2023”. Ms. Sroka added that the purchase and operation of Pegasus had “no basis” in law. The parliamentary committee will examine the objectives and legality of the use of Pegasus and try to establish how it and other similar systems were acquired by Poland.‘Long list’
According to several sources within the new governing coalition, led by pro-EU Prime Minister Donald Tusk, the undisclosed list of individuals to be questioned could be “very long” and “shocking”. Citizen Lab, a Canada-based cybersecurity monitoring group, claimed that Pegasus was used against several people in Poland. One notable target, they say, was Krzysztof Brejza, currently a member of the European parliament but previously a coordinator of the electoral campaign of an opposition party, Civic Platform, during 2019 legislative elections. Read More:- https://www.thehindu.com/news/international/polands-right-wing-leader-questioned-over-pegasus-spyware/article67957179.ece Source Credit: https://www.thehindu.com/news/international/
Polish investigators seize Pegasus spyware systems as part of probe into alleged abuse
Polish prosecutors have seized Pegasus spyware systems from a government agency in Warsaw and are now studying them to “determine the functionality of the Pegasus software and the broad legality of its use,” a spokesperson for the National Prosecutor’s Office said Friday according to local news reports.
The prosecutor’s office inspected and secured devices related to the powerful commercial surveillance tool at the headquarters of the Central Anticorruption Bureau on Tuesday and Wednesday, the spokesperson said.
The operation is part of a national scandal in which the previous Polish government is accused of widely abusing Pegasus to spy on opposition politicians.
Investigators also took documents from the Central Anticorruption Bureau, the Internal Security Agency, the Military Counterintelligence Service and the Police “regarding the purchase of Pegasus software, its functionality and use as part of operational inspections," the spokesperson said.
"The obtained data was transferred to the Forensic Research Office of the Internal Security Agency, which was appointed to issue an opinion on the operation and functionality of the Pegasus system," he added.
The National Prosecutor’s announced in March that it had begun a probe examining the prior majority’s use of Pegasus from November 2017 to December 2022.
Investigators are now focused in part on who purchased Pegasus for the Polish authorities.
Former Deputy Prime Minister Jarosław Kaczyński; former Deputy Minister of Justice Michał Woś; former director of the Department of Family and Juvenile Affairs at the Ministry of Justice Mikołaj Pawlak; and other Ministry of Justice employees have testified so far, according to local news reports.
Pegasus is manufactured by an Israeli company known as the NSO Group and has been increasingly showing up on the phones of civil-society figures in countries as far flung as Spain, Poland, Rwanda, Hungary, Mexico, Thailand and Latvia.
In April, Poland’s justice minister announced that nearly 600 people there, mostly opposition politicians and their allies, were targeted for surveillance with Pegasus under the former ruling Law and Justice (PiS) party.
Despite abuses such as those surfacing in Poland, NSO Group has defended the use of Pegasus on phones belonging to opposition “political operatives.”
Responding to Friday’s news, John Scott-Railton, a senior digital forensics researcher at The Citizen Lab, which helped uncover the abuse of Pegasus in Poland, tweeted: “Win for transparency in Poland. Nightmare for NSO Group.”
In September, Poland's Senate unveiled findings from a special commission’s investigation into the use of Pegasus to hack an opposition politician in 2019, saying the incident involved "gross violations of constitutional standards.”
The commission said it had notified prosecutors there of the potential for criminal charges against current and former Polish ministers who have been implicated in the use of the spyware.
The investigation, which ran across 18 months, also determined that the 2019 elections involving hacked opposition leader Senator Krzysztof Brejza were unfair due to use of the spyware.
“Pegasus is not an operational tool used by the services, but it is a cyber weapon, i.e. a tool to influence the behavior of other people,” Pegasus Surveillance Committee Chairman Marcin Bosacki said according to a summary report. “We can unequivocally state that Pegasus was used in Poland to an extremely aggressive degree.”
Read More:- https://therecord.media/poland-seizure-pegasus-spyware-systems?&web_view=true Source Credit: https://therecord.media/
Chinese shopping app ‘is spying on Western customers’
New “Snowblind” Android Malware Steals Logins, Bypasses Security Features

Spyware maker NSO Group claims politicians are ‘legitimate’ spying targets

Three Android spyware apps detected on Google Play Store

Mercenary spyware: Apple says iPhone users in India and 91 other countries were likely victims of a spyware
Apple warns iPhone users in India and 91 other countries about potential spyware attacks. The company previously sent similar warnings to Indian politicians, suggesting possible state-sponsored spyware attacks.
Apple recently sent out warnings to iPhone users in India and 91 other countries. The company informed users saying that their iPhones might be under attack by a type of spyware called "mercenary spyware," including one called Pegasus made by a company called NSO Group in Israel. Last October, they sent similar warnings to politicians from different parties in India, suggesting a possible state-sponsored spyware attack on their iPhones. However, Apple later said they couldn't pinpoint any specific attacker. According to an Indian Express report.These warnings came without blaming anyone for the attacks. The warning emails were sent out around 12:30 am IST on a Thursday. It's not clear how many people got them. The emails mentioned Pegasus spyware and said that similar tools are being used globally to target people. The subject line of the email read "ALERT: Apple detected a targeted mercenary spyware attack against your iPhone." Apple explained in the email that these attacks are rare and very sophisticated, costing lots of money and targeting only a few people. They advised users to be careful with links and attachments from unknown senders. “Apple detected that you are being targeted by a mercenary spyware attack that is trying to remotely compromise the iPhone associated with your Apple ID -xxx-. This attack is likely targeting you specifically because of who you are or what you do. Although it’s never possible to achieve absolute certainty when detecting such attacks, Apple has high confidence in this warning — please take it seriously,” the email read. “Mercenary spyware attacks, such as those using Pegasus from the NSO Group, are exceptionally rare and vastly more sophisticated than regular cybercriminal activity or consumer malware. These attacks cost millions of dollars and are individually deployed against a very small number of people, but the targeting is ongoing and global,” Apple said in its threat notification. Apple couldn't give more details about why they sent the warnings because it might help the attackers avoid detection. They updated their support page to help users who might be targeted. Apple started sending these warnings in 2021, and people from 150 countries have received them. Last year, at least 20 Indians with iPhones got these warnings too. Previous investigations into similar issues haven't had much success. In 2021, the Supreme Court in India formed a committee to look into allegations of illegal surveillance using Pegasus. However, they didn't find clear evidence, partly because the government didn't cooperate.Overall, Apple wants its users to be aware of the risks of such attacks and stay safe online. Read More:- https://www.indiatoday.in/technology/news/story/mercenary-spyware-apple-says-iphone-users-in-india-and-91-other-countries-were-likely-victims-of-a-spyware-2525965-2024-04-11 Source Credit: https://www.indiatoday.in/technology/news/story/
‘State-sponsored’ attacks on phones of India opposition leaders, says Apple

Pegasus-like spyware attack likely on select individuals, warns Apple

Spyware attack on iPhones erodes trust in mobile phones
How to stay safe
Harish Kumar asked the users to ensure their phones were running on the latest iOS version. “Apple releases frequent security updates to patch vulnerabilities exploited by attackers. One needs to update the software,” he said. Phishing emails and messages are often used to deliver spyware. “Be cautious of unsolicited messages, even if they appear to come from a known contact. Never click on suspicious links or download attachments from untrusted sources,” he said. He recommended the users to go for Multi-Factor Authentication (MFA) for all their online accounts, including the Apple ID to get an extra layer of security. “When installing new apps, one should carefully review the permissions they ask for. You must give access to features genuinely needed for the app’s functionality,” he said. Besides backing up the data regularly, one should have a strong password and avoid accessing the internet using public Wi-Fi networks. Kiran Chandra, however, felt that one could do little if one is attacked by powerful such as Pegasus spyware. Read More:- https://www.thehindubusinessline.com/info-tech/spyware-attack-on-iphones-erodes-trust-in-mobile-phones/article68061580.ece Source Credit: https://www.thehindubusinessline.com/info-tech/
Is your mobile phone hacked? Know warning signs and immediate actions to take

Pegasus infection found on Indian journalists’ phones after Apple alert: Amnesty International
Amnesty International announced that it found recent traces of Pegasus spyware, sold only to governments, on two Indian journalists’ phones after they received “state-sponsored attacker” alerts from Apple in October.
The Wire news website’s founder editor, Siddharth Varadarajan, and another journalist in India were targeted with Pegasus spyware this year, the nonprofit Amnesty International’s Security Lab was able to determine after testing their devices, it announced on Thursday. The journalists had received an alert from Apple that they were being targeted by “state-sponsored hacking,” following which they provided their phones to Amnesty for testing. NSO Group, the Pegasus spyware’s developer, only sells its technology to governments. India’s Intelligence Bureau imported hardware from NSO Group in 2017, trade data show. Separately, TheWashington Post reported that after the security alerts went out in October, government officials put ‘pressure’ on Apple to offer ‘alternative’ explanations to the public on why these warnings were sent to Opposition leaders and journalists. Union Ministers and Apple had made a series of misleading and unsubstantiated statements when these alerts went out, such as that these messages had gone out in 150 countries, when no other countries’ citizens — or ruling party lawmakers — had reported receiving a warning that week. According to the Post report, Praveen Chakravarty, the chairman of the All India Professionals’ Congress, was also likely targeted, based on an analysis of his phone by iVerify, a cybersecurity firm. The Pegasus spyware, which the Union government has not categorically denied buying or using, allows attackers to extract all the contents of smartphones by leveraging software weaknesses that are known to a select few hackers, and sold for millions of dollars. These so-called ‘zero day exploits’ allow attackers to access all the data on even phones whose software has been fully updated, and access real-time camera and microphone data. Such technology, privacy activists argue, is an unconstitutional form of surveillance. Dozens of Opposition leaders, journalists and activists were targeted by Pegasus until 2021, according to the Forbidden Stories collective, which reported on a leak of the spyware’s global targets.‘Attack on privacy’
“Targeting journalists solely for doing their work amounts to an unlawful attack on their privacy and violates their right to freedom of expression. All states, including India, have an obligation to protect human rights by protecting people from unlawful surveillance,” said Donncha Ó Cearbhaill, head of the Security Lab that uncovered the infections. “The recovered samples are consistent with the NSO Group’s BLASTPASS exploit, publicly identified by Citizen Lab in September 2021 and patched by Apple in iOS 16.6.1 (CVE-2023-41064),” Amnesty said in a statement, referring to a vulnerability that Apple patched through a software update in September. The Union government refused to cooperate in a Supreme Court-ordered investigation into the 2021 Pegasus revelations. Both Mr. Varadarajan and Anand Mangnale, South Asia Editor at the Organised Crime and Corruption Report Project (OCCRP), had spyware that logs show infected their phones this year. The OCCRP had reported last year that the Intelligence Bureau (IB) obtained Pegasus, citing trade data that The Hindu was later able to verify, and interviews with unnamed IB officers. Ten months later, Mr. Mangnale’s phone was infected, Amnesty found. The day before, he told TheWashington Post, he had sent queries to the Adani group for an investigative story OCCRP was working on about the corporate group. Mr. Varadarajan’s phone was found to be infected on October 16. Both men received alerts from Apple in October saying that their phones had been targeted by “state-sponsored attackers”. The Union government said it was investigating these alerts, which were sent to numerous Opposition members of Parliament as well. The Union government was reportedly looking for Pegasus alternatives after the NSO Group’s activities came under global scrutiny, but the spyware’s continued use after the furore has only emerged now. The Defence Intelligence Agency’s Signal Intelligence Directorate has purchased equipment from Cognyte, a company that has been sued in the United States on similar snooping grounds, The Hindu had reported in April. Read More:- https://www.thehindu.com/news/national/pegasus-infection-found-on-indian-journalists-phones-after-apple-alert-amnesty-international/article67682427.ece Source Credit: https://www.thehindu.com/news/national/
IPhone, Android users warned of dangerous ‘zero-click’ attacks – here’s a simple method to protect yourself
Android and iPhone users are being urged to reboot their devices once a week to help prevent hackers from sneaking spyware onto their phones via 'zero-click' exploits.
As the name suggests, zero-click attacks don't require a user to click on a malicious link or download a compromised file. Instead, malware is installed on a device without any interaction from the victim, leaving little trace and making detection very difficult. A zero-click hack will exploit flaws or vulnerable areas in your phone, such as using a data verification loophole to infiltrate your system. According to the cybersecurity company Kaspersky, these attacks often target apps that offer messaging or voice calling because they are designed to receive and interpret data from untrusted sources. For example, hackers could use a hidden text message or image file to inject code that compromises the device, allowing them to install spyware and collect data, Kaspersky warns. They could also infect a device by manipulating opened URLs. However, turning your phone off and on again every week can help protect against such attacks, as it temporarily deletes the information that continuously runs in the background via apps or an internet browser. The method does require the user to reboot their phone - not simply placing it in standby mode. The method is endorsed by the US National Security Agency (NSA), which detailed the steps iPhone and Android users should take to mitigate the risk of a cyberattack in a comprehensive document. A simple reboot can also mitigate the threat of spear-phishing, a type of phishing attack that typically targets individuals or organisations through malicious emails. The goal of spear-phishing is to install malware and spyware on the targets' device, or steal sensitive information such as login credentials. The document also recommended disabling Bluetooth when it's not in use, not connecting to public Wi-Fi networks, removing any unused networks, avoiding email attachments or links from an unknown source, and updating software and apps regularly. Keeping your software and applications up to date will ensure any potential flaws or loopholes in the old version are removed, in turn making your device more secure. It also recommended setting up a strong PIN - six-digit minimum - and enabling additional security measures, such as the phone factory-resetting itself after 10 incorrect passcode entries. While the tips won't 100 percent guarantee protection from hacks and breaches, it should provide some defence against certain types of attacks, the NSA noted. Turning the phone off and on again will also not help against more advanced malware threats, which are programmed to reload on reboot. "Threats to mobile devices are more prevalent and increasing in scope and complexity," the agency warned, adding that some smartphone features "provide convenience and capability but sacrifice security". "Falling for social engineering tactics, like responding to unsolicited emails requesting sensitive information, can result in account compromise and identity theft," Oliver Page, the CEO of cybersecurity company Cybernut, told Forbes. "These phishing attempts often mimic legitimate entities, deceiving individuals into divulging confidential details. "Trusting phone calls or messages without verification can lead to serious consequences, as scammers manipulate victims into disclosing sensitive information or taking actions that compromise their security." According to reports, the last major zero-click exploit occurred in 2021, in which hackers targeted an image-processing vulnerability in Apple's iMessage app. The attack was able to bypass Apple's BlastDoor security feature, leading some researchers to call the exploit "one of the most technically sophisticated" they'd seen. Apple filed a lawsuit against NSO Group, an Israeli cyber-arms company primarily known for its extremely controversial malicious spyware Pegasus, which is capable of zero-click exploits and other sophisticated attacks. The spyware is designed to be covertly and remotely installed on mobile phones running iOS or Android. Read More:- https://www.newshub.co.nz/home/lifestyle/2024/06/iphone-android-users-warned-of-dangerous-zero-click-attacks-here-s-a-simple-method-to-protect-yourself.html Source Credit: https://www.newshub.co.nz/home/lifestyle/2024/06/
NSA says you should restart your phone every week: Here’s why
According to Forbes, a recently revealed NSA document dating years back shares best practices for keeping your smartphone safe from threat actors and suggests that restarting your phone now and then can help with some zero-day exploits and malware that might be running on your phone. NSO Group, the company behind the Pegasus spyware is also known for using zero-day exploits to spy on its targets.

Spy agency issues urgent warning to billions of smartphone users to avoid being spied on

Journalists, lawyers and activists hacked with Pegasus spyware in Jordan, forensic probe finds
What is the Pegasus spyware scandal and how is Singapore affected?

Apple warns: Users in India and 91 other countries impacted by “mercenary spyware” attack

EU failure to rein in spyware reflects lack of political will, parliamentarian says

Is Pegasus spyware targeting journalists in India?